In today’s rapidly evolving threat landscape, organizations need more than just security implementations—they need measurable outcomes. A zero trust framework analysis provides a systematic approach to evaluate how your people, processes, and technologies align with zero trust principles. This practical guide will equip security leaders with actionable metrics and methods to measure cybersecurity model effectiveness, demonstrate ROI, and continuously improve your security posture. What is Zero Trust Framework Analysis?

The zero trust framework operates on the principle of “never trust, always verify” across all network components
Zero trust is a security philosophy that assumes no implicit trust—whether the actor is inside or outside the corporate network—and requires continuous verification of identity, device posture, and access requests. A zero trust framework analysis is a systematic review that evaluates how an organization’s people, processes, and technologies align with zero trust principles (identity-first controls, least-privilege access, micro-segmentation, and continuous monitoring).
“Never trust, always verify” is more than a slogan—it’s a measurable approach to reducing risk across a distributed environment.
For authoritative guidance, security professionals should reference the NIST Zero Trust Architecture standard: NIST SP 800-207. This framework provides the foundation for implementing and measuring zero trust effectiveness.
Why Measuring Cybersecurity Model Effectiveness Matters
Organizations invest in zero trust security models to lower breach risk, improve compliance, and enable business agility for cloud adoption and remote work. However, without measurable outcomes, these investments remain assumptions. A disciplined zero trust effectiveness evaluation helps:
- Tie security activities to business objectives and regulatory obligations
- Quantify improvements in reduced attack surface and faster threat containment
- Prioritize remediation where it yields the highest return on security investment
- Demonstrate tangible ROI to executive leadership and boards
- Create a baseline for continuous improvement and adaptation
Core Components of a Zero Trust Architecture Review
A thorough zero trust architecture review examines these essential domains to identify gaps and prioritize improvements:
Identity & Access Management
Evaluates MFA implementation, adaptive authentication methods, and identity lifecycle management processes.
Device Posture & Endpoint Security
Assesses endpoint detection and response (EDR) capabilities, device health verification, and patch management.
Network Segmentation
Reviews micro-segmentation strategies that break lateral movement paths and limit potential breach impact.
Least-Privilege Access Controls
Examines role-based or attribute-based policies that minimize privileges and reduce the attack surface.
Continuous Monitoring
Evaluates telemetry, behavioral analytics, and logging capabilities for real-time security decisions.
Policy Engine & Enforcement
Analyzes policy decision and enforcement architecture that acts on signals from across the environment.
An architecture review reveals gaps—for example, strong identity controls but poor device telemetry—which directly informs a prioritized remediation plan.
Types of Zero Trust Security Models and Their Trade-offs
Zero trust can be approached from different focal points, each with distinct advantages and limitations:
Network-centric Approach
- Clear boundaries for network traffic
- Familiar to network security teams
- Strong control over data flows
- Compatible with existing network tools
Network-centric Limitations
- May struggle in cloud-native workloads
- Less effective for identity-driven access
- Can be complex to implement at scale
- Potential performance impacts
Identity-centric Approach
- Well-suited to hybrid clouds and remote work
- Identity is the primary control plane
- Adaptable to changing work environments
- User-focused security model
Identity-centric Limitations
- Requires comprehensive identity hygiene
- Needs strong telemetry integration
- May miss network-level threats
- Identity provider dependencies
Workload-centric Approach
- Excellent for cloud-native environments
- Service mesh and container policy integration
- Application-level security controls
- DevOps-friendly implementation
Workload-centric Limitations
- Requires DevSecOps integration
- More complex for traditional applications
- May miss user-level threats
- Steeper learning curve
Most effective zero trust programs combine approaches: identity-first controls for access, network segmentation for lateral defense, and workload controls for cloud-native applications.
Common Misconceptions About Zero Trust
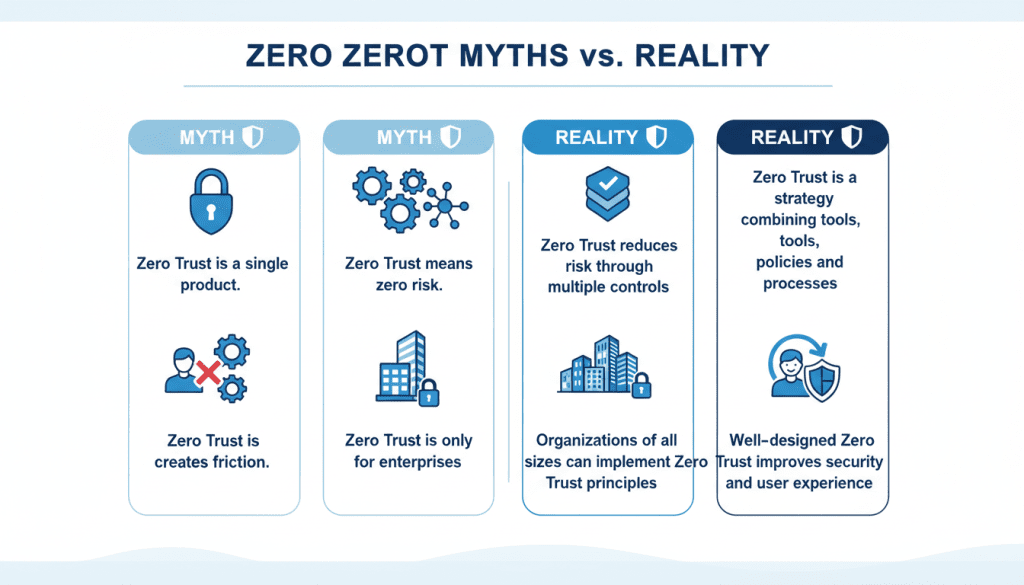
- Zero trust is not a single product. It’s a strategy that combines tools, policies, and processes.
- Zero trust does not mean zero risk. It reduces risk by constraining attack surfaces and improving detection and response.
- Zero trust is not only for large enterprises. Small and medium businesses can adopt zero trust principles scaled to risk and resources.
- Zero trust is not inherently disruptive to users. Well-designed implementations can enhance both security and user experience.
Common pitfalls: Overemphasis on technology, ignoring user experience, or failing to measure outcomes—all hinder effective implementation and evaluation.
Metrics and Methods for Zero Trust Effectiveness Evaluation
Quantitative Metrics for Measuring Security Success
Good measurement uses objective, repeatable metrics. Typical KPIs for a zero trust effectiveness evaluation include:
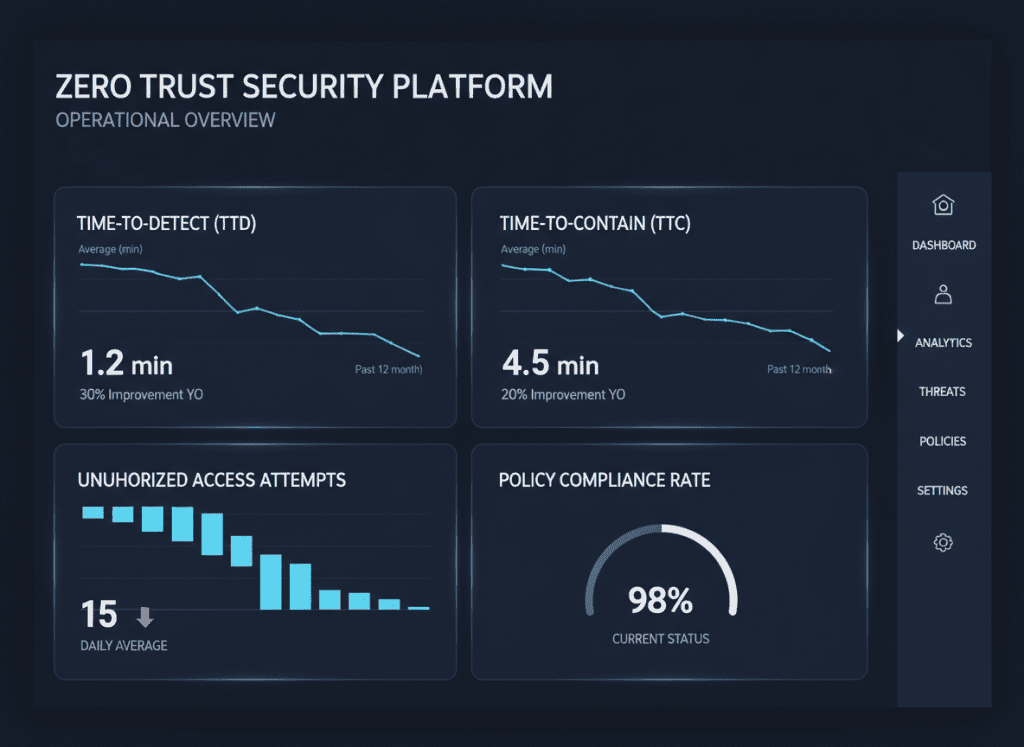
| Metric | Definition | Baseline Example | Target Example | Data Source |
| Time-to-Detect (TTD) | Median time from intrusion to detection | 72 hours | 24 hours | SIEM/EDR |
| Time-to-Contain (TTC) | Median time from detection to containment | 48 hours | 4 hours | SOAR/Ticketing |
| Incident Frequency | Number of security incidents per quarter | 24 | 12 | Incident Database |
| Unauthorized Access Attempts | Blocked access attempts by identity/device | 1,200/month | 600/month | IAM/ZTNA Logs |
| Attack Surface Reduction | Exposed services or privileged accounts eliminated | 850 | 425 | Vulnerability Scanner |
| Policy Compliance Rate | % of access requests governed by zero trust policies | 65% | 95% | Policy Engine |
Example KPI definition (JSON snippet):
{
"kpi": "time_to_detect",
"definition": "Median hours from intrusion start to detection",
"baseline": 72,
"target": 24,
"data_source": "SIEM/EDR"
} Ready to measure your zero trust effectiveness?
Download our Zero Trust KPI Dashboard Template to start tracking your security metrics and demonstrate measurable improvements to stakeholders.
Download KPI Dashboard Template
Qualitative Assessment Methods
Quantitative metrics need context from qualitative methods to provide a complete picture:
Risk Assessments
Map assets to business impact and identify high-value targets that require enhanced protection. This provides context for prioritizing zero trust controls.
Maturity Models
Use frameworks like CISA’s Zero Trust Maturity Model to gauge organizational readiness across multiple dimensions of zero trust implementation.
Stakeholder Interviews
Capture operational friction and business priorities from IT, HR, legal, and application owners to ensure zero trust controls align with business needs.
Red/Blue Team Exercises
Validate detection, containment, and operational playbooks through simulated attacks that test the effectiveness of your zero trust controls.
Combining quantitative and qualitative inputs gives a more complete view of measuring security success that includes business impact and user experience.
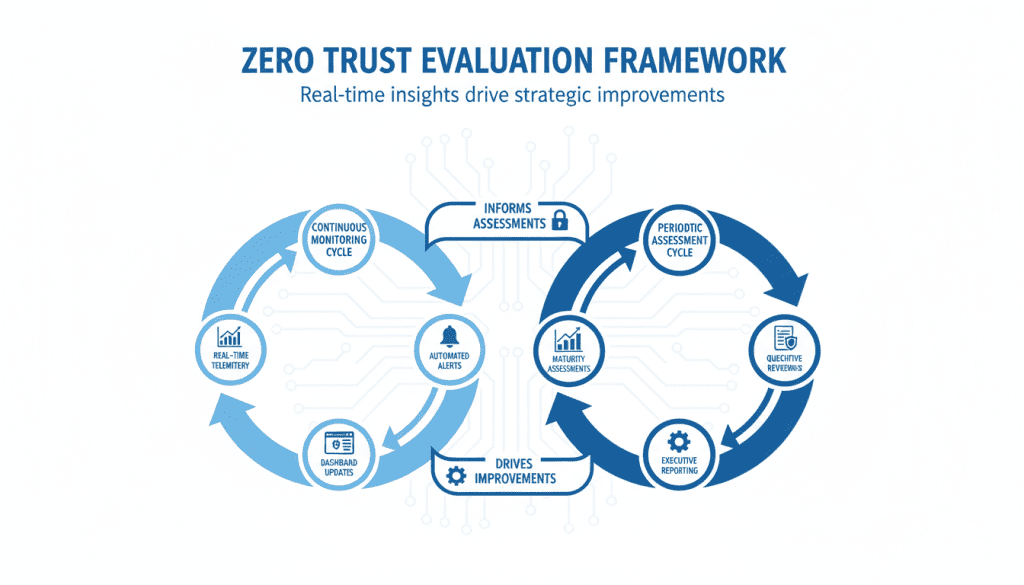
Designing an Evaluation Framework
A practical evaluation program blends continuous telemetry with periodic reviews:
- Continuous monitoring: Implement SIEM, EDR, and network telemetry feeding real-time dashboards
- KPIs & SLAs: Define thresholds and escalation paths for each key performance indicator
- Architecture reviews: Conduct quarterly deep-dives on identity, network, and workload controls
- Reporting cadence: Establish weekly operational reports, monthly executive summaries, and quarterly board-ready analytics
Dashboard examples and reporting cadence:
- Operational dashboard: Live TTD/TTC, active incidents, policy violation heatmap — updated hourly
- Tactical dashboard: Weekly trends, top 10 risky assets, failed MFA attempts — updated daily/weekly
- Executive report: Quarterly ROI, residual risk posture, compliance status — presented to CISO and board
Implementing Zero Trust Strategies: From Plan to Operation
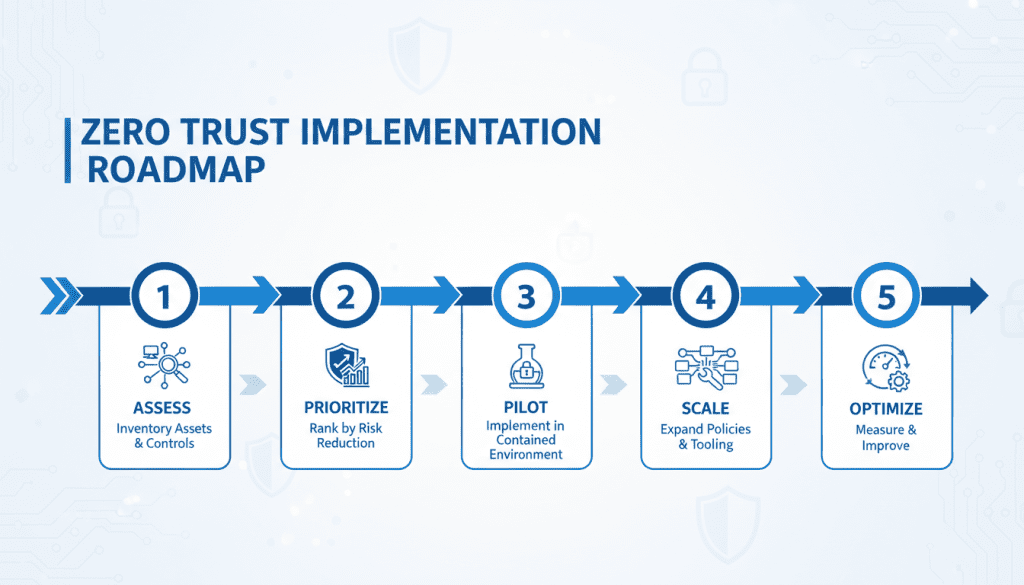
Roadmap for Implementing Zero Trust Strategies
A phased approach reduces risk and builds momentum when implementing zero trust:
- Assess: Inventory assets, users, and existing controls; conduct a zero trust framework analysis
- Prioritize: Rank controls by risk reduction and feasibility (e.g., MFA for admin accounts first)
- Pilot: Implement in a contained environment (e.g., a business unit or cloud workload)
- Scale: Expand policies and tooling based on pilot lessons
- Optimize: Measure outcomes, tune policies, and invest in automation
Align implementation with business objectives and compliance needs (e.g., HIPAA, GDPR, CMMC) to ensure resources map to both risk and regulation.
Need a structured approach to zero trust implementation?
Get our 90-Day Zero Trust Pilot Plan template with week-by-week activities, milestones, and measurement checkpoints.
Download 90-Day Pilot Plan
Integration and Interoperability Challenges
Common technical challenges when implementing zero trust include:
Legacy Systems
Unsupported protocols and devices lack modern telemetry. Consider network segmentation or compensating controls.
Identity Federation
Multiple identity providers or inconsistent attributes complicate policy enforcement and create potential security gaps.
Tooling Fragmentation
Many point solutions produce telemetry silos that make comprehensive monitoring difficult.
Best Practices for Seamless Integration:
- Adopt open standards (SAML, OIDC, SCIM) for identity integration
- Centralize telemetry into a SIEM or analytics platform
- Start with critical control planes (identity, device posture) before full-stack replacement
- Create cross-functional teams that include network, security, and application owners
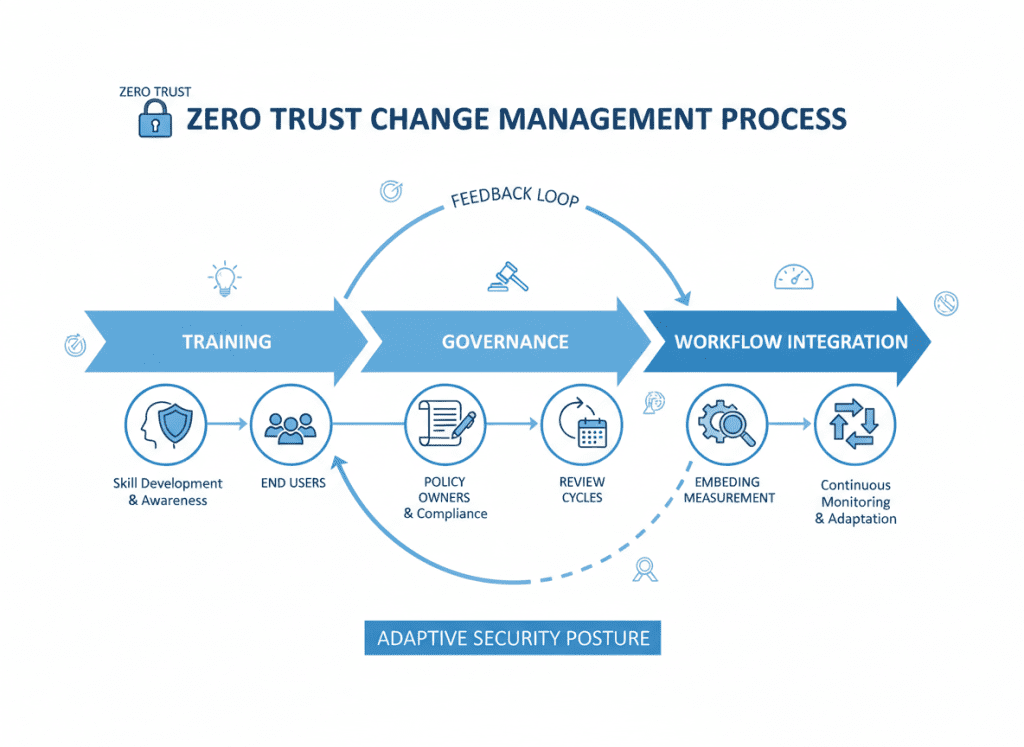
Change Management and Operationalizing Measurements
People and processes are critical to zero trust success:
Training
Implement regular role-based training for administrators, developers, and end users to ensure understanding of zero trust principles and practices.
Governance
Define clear owners for policies, controls, and KPIs to ensure accountability and consistent application of zero trust principles.
Policy Updates
Keep access policies aligned to business changes such as mergers, new applications, or organizational restructuring.
Workflows
Embed measurement into security operations by making KPI review part of incident postmortems and regular security team meetings.
Embedding measurement in daily workflows changes zero trust from a project to an operating model.
Case Studies and Comparative Analysis
Success Story: Zero Trust Framework Analysis in Financial Services
Context
A large U.S. bank faced frequent credential-stuffing attempts and had a complex hybrid cloud environment with hundreds of applications.
Actions Taken
- Performed comprehensive zero trust framework analysis
- Prioritized MFA for all privileged and third-party accounts
- Implemented conditional access based on device health and location
- Micro-segmented internal services to limit lateral movement
- Deployed continuous monitoring with behavioral analytics
Measured Outcomes
- 70% reduction in successful unauthorized access attempts
- Time-to-detect improved from 96 hours to 18 hours
- Incident severity ratings dropped by 40%
- Improved compliance posture for regulatory audits
- Reduced expected breach cost exposure by $3.2M
Common Failure Modes and Remediation
Scenario: Public-Sector Organization Cloud Migration
Failure Mode
- Adopted new tooling without end-to-end telemetry integration
- Policies were inconsistent across departments
- Excessive privileges remained despite new controls
- Limited visibility into cloud workload activity
Consequences
- Continued lateral movement in security incidents
- Long containment times (average 72+ hours)
- Fragmented security posture across environments
- Compliance gaps for sensitive data
Remediation
- Conducted zero trust architecture review
- Eliminated stale admin accounts (50% reduction)
- Standardized policy templates across departments
- Centralized logging and implemented SOAR playbooks
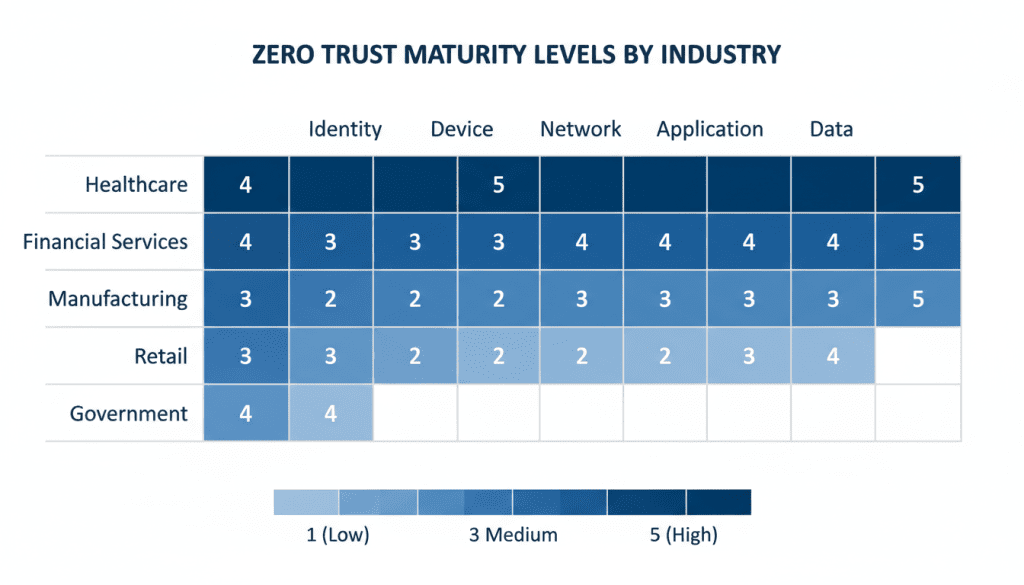
Comparative Benchmarking Across Industries
Effectiveness varies by sector and scale. Here’s how different industries approach zero trust:
Healthcare
Challenges: High regulatory burden (HIPAA), legacy medical devices
Approach: Identity-centric zero trust with strong data protection
Benchmarks: 40-60% reduction in unauthorized access within first year
Financial Services
Challenges: Sophisticated threats, complex application landscape
Approach: Strong IAM and micro-segmentation with behavioral analytics
Benchmarks: 50-70% improvement in threat detection time
Manufacturing/OT
Challenges: IT/OT convergence, availability requirements
Approach: Network-centric with strict segmentation between IT and OT
Benchmarks: 30-50% reduction in potential attack paths
Organizations should use industry reports and internal baselines for comparison. Typically, companies aim to lower TTD/TTC by 30–50% in the first year of a zero trust program.
Advanced Topics and Future Directions
Automation and AI in Measuring Security Success
Automation and AI accelerate continuous evaluation of zero trust effectiveness:
- Automated threat detection: ML models improve anomaly detection and reduce time-to-detect by identifying patterns humans might miss
- Policy automation: Dynamic access policies based on risk signals (device health, location, behavior) that adapt in real-time
- Automated remediation: Orchestrated playbooks reduce time-to-contain by automating routine response actions
Governance considerations: Avoid blind trust in models — validate and tune ML systems. Maintain human oversight for high-risk decisions and compliance reporting.
Evolving Threats and Adapting Zero Trust Models
Threat trends affecting zero trust implementation and measurement:
Current Threat Trends
- Increased supply-chain attacks and compromised third-party credentials
- More sophisticated lateral movement techniques in cloud-native environments
- Identity-based attacks targeting federation trust relationships
- AI-powered social engineering to bypass authentication
Iterative Adaptation Approaches
- Continually update threat models and security assumptions
- Refresh segmentation strategies based on new attack techniques
- Prioritize patches for vulnerabilities in authentication systems
- Use red-team exercises to validate controls and assumptions
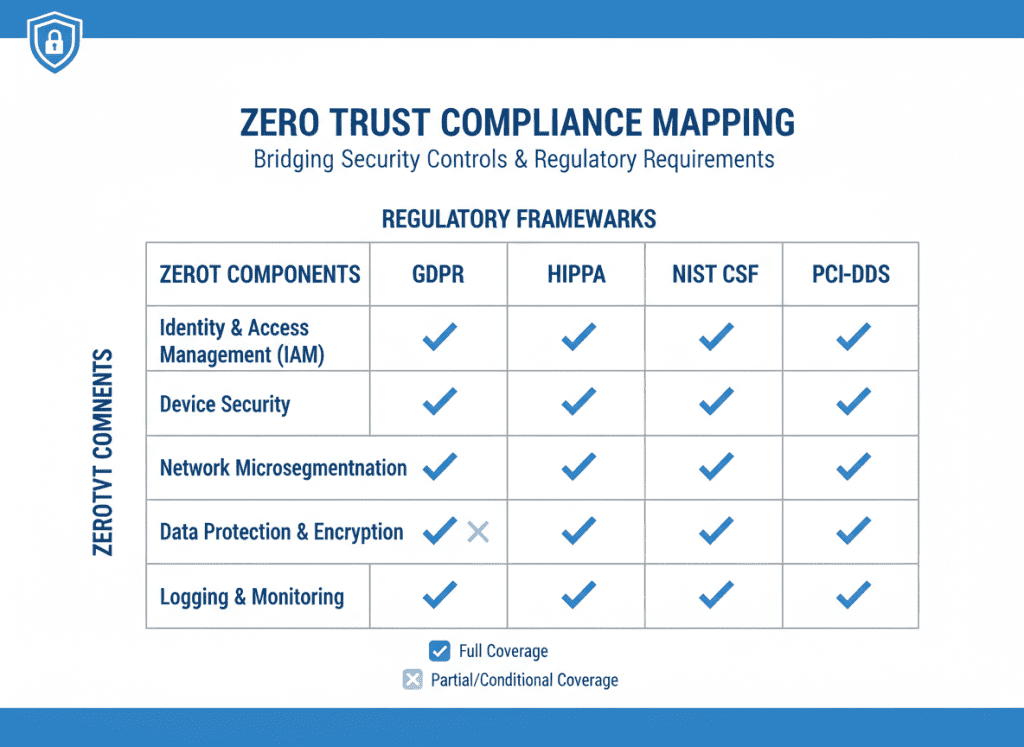
Regulatory and Compliance Implications
Regulations increasingly shape zero trust architecture review and reporting requirements:
- GDPR and HIPAA require demonstrable access controls and breach response readiness
- Federal agencies (U.S.) increasingly expect zero trust alignment as part of cybersecurity mandates
- Industry-specific regulations often map directly to zero trust principles
Incorporate compliance metrics into your zero trust effectiveness evaluation:
- Policy enforcement rates for regulated data
- Audit-ready logs retention and access review cadence
- Documentation of security controls mapped to compliance requirements
For federal agencies and their partners, refer to CISA’s Zero Trust Maturity Model for guidance on compliance alignment.
Conclusion: Key Takeaways for Evaluating Zero Trust Security Models
- A zero trust framework analysis should be measurable: define objectives, pick KPIs, and baseline current posture
- Combine quantitative metrics (TTD, TTC, incident frequency) with qualitative assessments (maturity models, stakeholder interviews)
- A phased roadmap (assess → prioritize → pilot → scale → optimize) reduces risk and improves adoption
- Address interoperability and change management: identity federation, legacy systems, and governance are common blockers
- Use automation and continuous monitoring to reduce measurement latency — but govern ML and automation carefully
- Regulatory frameworks increasingly expect evidence of controls; incorporate compliance KPIs into your zero trust effectiveness evaluation
Next Steps: Start Measuring and Improving Now
- Conduct a focused zero trust framework analysis for a high-risk business domain (e.g., admin accounts, customer data apps)
- Define 3–5 KPIs and set baselines from existing telemetry
- Run a pilot to validate policies and measure improvements
- Document results for stakeholders and iterate
For practical guidance, consult these authoritative resources:
Ready to evaluate your zero trust implementation?
Download our industry-specific Zero Trust Architecture Review Checklist to identify gaps and prioritize improvements in your security controls.
Get Your Architecture Review Checklist