
Strategies for Effective NIS2 Incident Management
January 13, 2026|10:15 AM
Unlock Your Digital Potential
Whether it’s IT operations, cloud migration, or AI-driven innovation – let’s explore how we can support your success.

January 13, 2026|10:15 AM
Whether it’s IT operations, cloud migration, or AI-driven innovation – let’s explore how we can support your success.
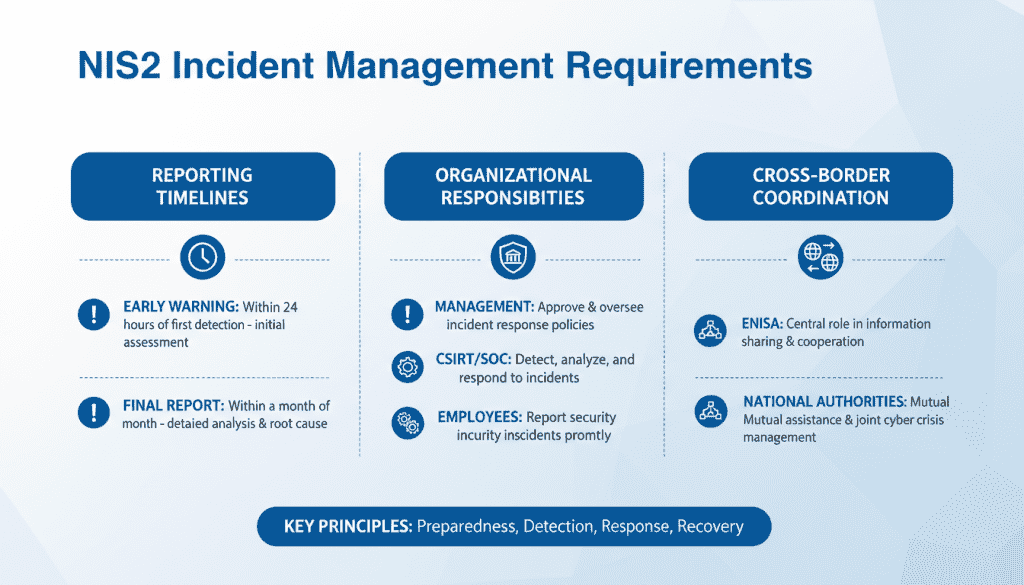
The Network and Information Systems Directive 2 (NIS2) represents a significant evolution in the EU’s cybersecurity framework. It expands regulatory scope, introduces stricter reporting obligations, and places direct accountability on senior management. For security professionals, this means adapting existing incident response frameworks to meet new compliance requirements while maintaining operational effectiveness.
NIS2 broadens the scope of entities subject to cybersecurity regulations across EU Member States, strengthens supervisory powers, and tightens reporting rules and enforcement. Member States were required to transpose the directive into national law by October 17, 2024, though some countries are still finalizing implementation details. The directive emphasizes both operational resilience and cross-border coordination, making incident handling a central compliance and business continuity concern.
NIS2 incident management encompasses the processes, roles, tools, and governance that ensure timely detection, handling, reporting, and learning from incidents in compliance with NIS2 obligations. While it overlaps with existing frameworks like ISO/IEC 27001 and NIST SP 800-61, NIS2 adds stricter reporting timelines and broader accountability for senior management.
NIS2 doesn’t replace existing incident response frameworks—it enhances them with specific regulatory requirements and timelines that must be integrated into your existing processes.
Key intersection points between NIS2 and established frameworks include:
Failing to meet NIS2 incident management requirements carries significant consequences:
Fines up to €10 million or 2% of global annual revenue for essential entities (€7 million or 1.4% for important entities)
Increased regulatory scrutiny, mandatory security improvements, and potential business disruption during remediation
Loss of customer trust, damage to brand reputation, and potential impacts on business relationships, especially with essential entities
According to the IBM Cost of a Data Breach Report, organizations with mature incident response capabilities reduce breach costs by an average of 58% compared to those without such capabilities. NIS2 compliance not only avoids penalties but also strengthens your overall security posture.
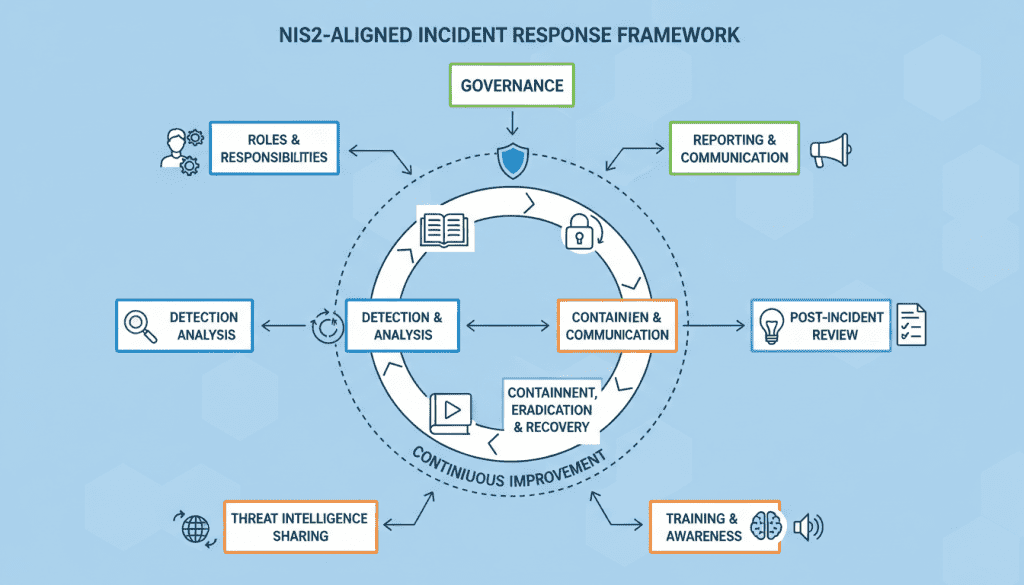
A comprehensive NIS2-aligned incident response program requires several interconnected components:
| Component | Description | NIS2 Alignment |
| Governance & Policy | Executive sponsorship, documented policies, and NIS2-compliant incident response procedures | Establishes management accountability and compliance foundation |
| Roles & Responsibilities | Clear RACI matrix for SIRT, CIO/CISO, Legal, Communications, and Business Continuity | Ensures timely decision-making and reporting within regulatory deadlines |
| Detection & Monitoring | 24/7 Security Operations Center (SOC), comprehensive logging, and threat intelligence | Reduces time-to-detect and enables early warning capabilities |
| Playbooks & Runbooks | Actionable procedures for common incident types with NIS2 reporting triggers | Standardizes response and ensures regulatory steps aren’t missed |
| Reporting & Evidence | Structured templates for timelines, impact assessment, and forensic artifacts | Facilitates 24/72-hour reporting requirements with proper evidence |
| Training & Exercises | Tabletop exercises and simulations that include NIS2 reporting scenarios | Validates team readiness for regulatory compliance under pressure |
| Continuous Improvement | Post-incident reviews and KPIs for maturity tracking | Demonstrates ongoing compliance and risk reduction to regulators |
Download our comprehensive NIS2 Incident Response Framework Template to jumpstart your compliance efforts.
Effective NIS2 incident management combines established security practices with specific regulatory requirements:
Implement comprehensive monitoring across endpoints, networks, and cloud assets to detect incidents earlier in the attack chain. This reduces time-to-detect and provides more time for analysis and reporting within NIS2 deadlines.
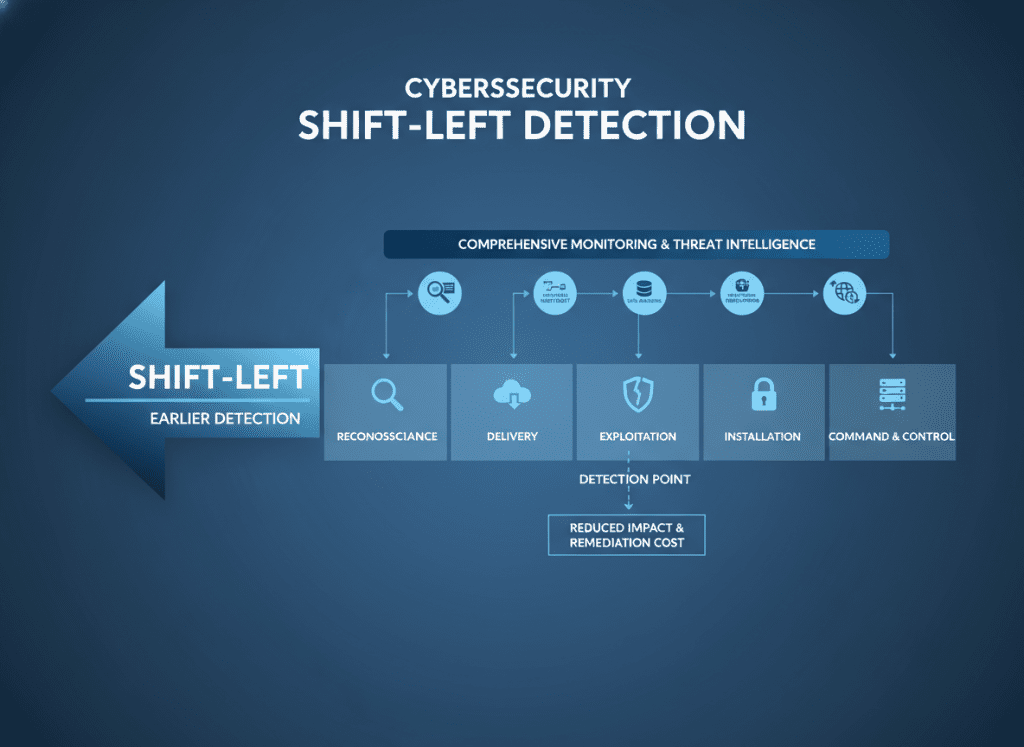
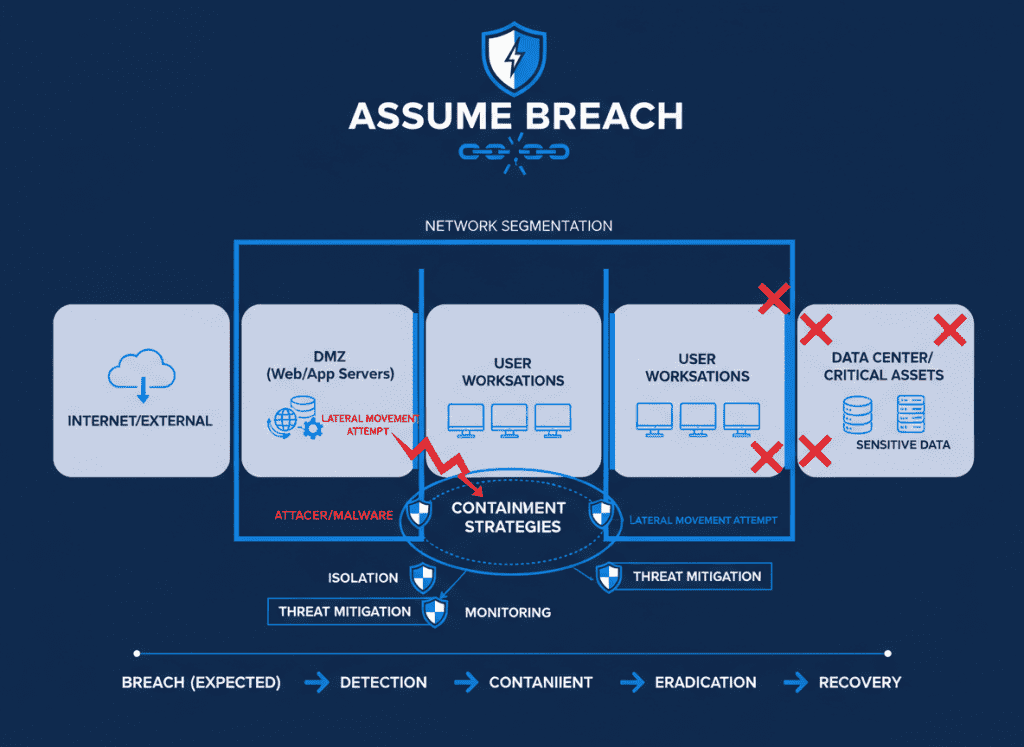
Design containment and segmentation strategies assuming attackers are already in your network. This approach minimizes lateral movement and reduces incident impact, which can affect NIS2 reporting thresholds and regulatory scrutiny.
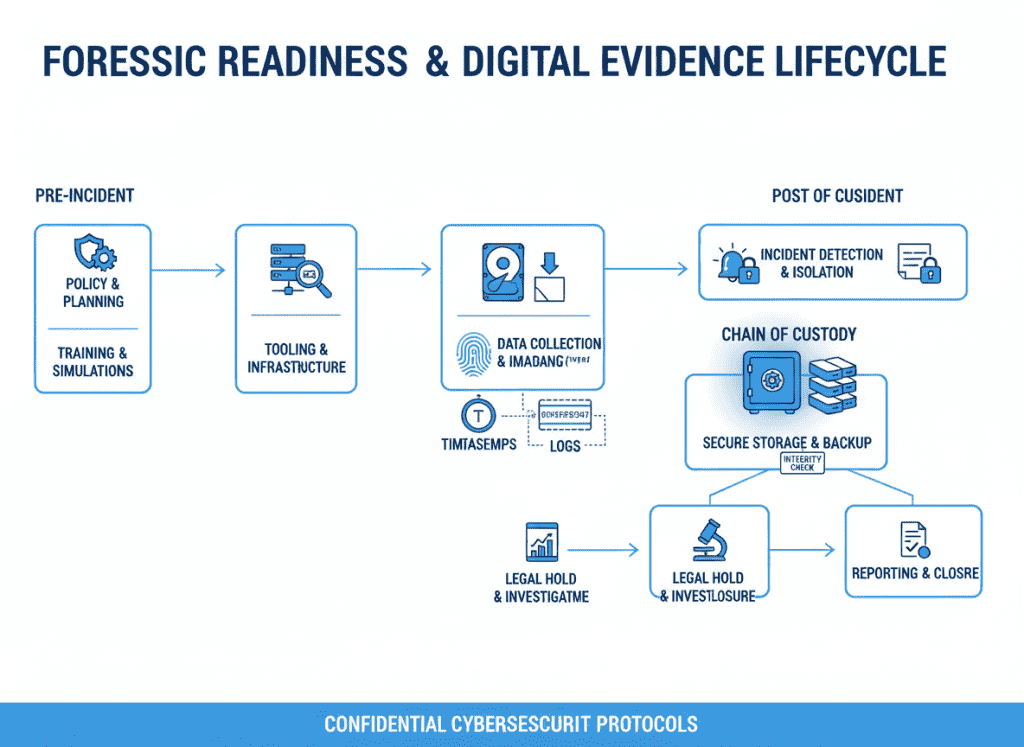
Maintain tamper-evident logs and artifact preservation procedures to ensure evidence survives regulatory review. NIS2 may require providing detailed incident timelines and impact assessments to authorities.
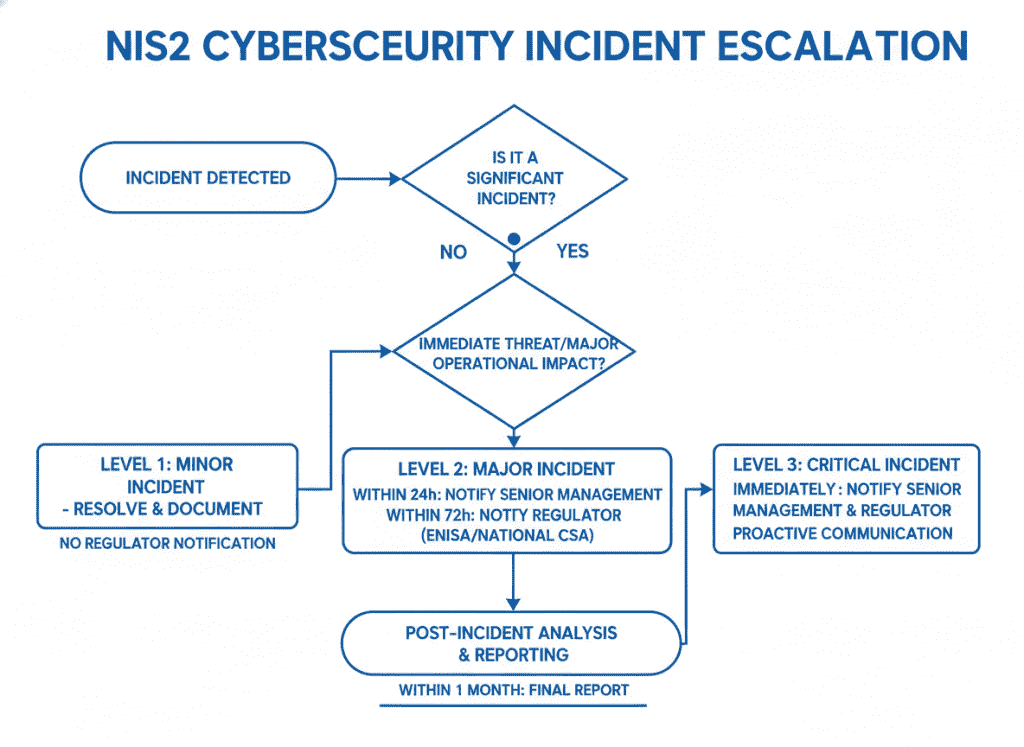
Implement automated thresholds that trigger senior leadership and regulator notification as required by NIS2. This ensures you never miss critical reporting deadlines even during high-stress incidents.
NIS2 incident management places importance on both technical defense and the completeness of documentation—treat documentation as a primary deliverable, not an afterthought.
Clear governance reduces response friction and ensures compliance with NIS2 reporting obligations:
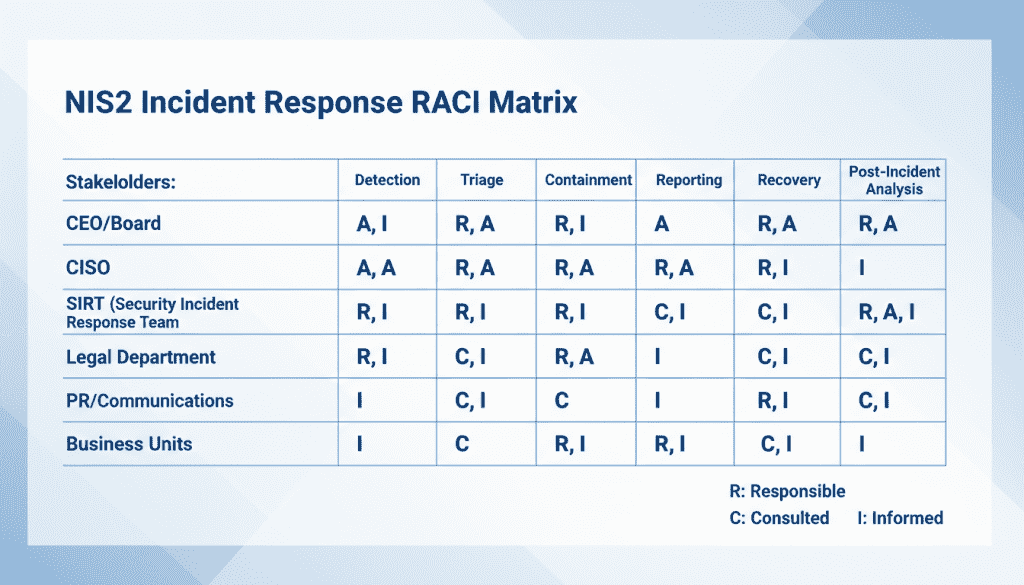
For high-impact incidents, establish a Senior Incident Decision Forum (SIDF) with:
This governance structure ensures that decisions are made at the appropriate level and that regulatory reporting obligations are never overlooked during crisis response.
Effective playbooks transform policy into actionable procedures. For NIS2 compliance, your playbooks should address both technical response and regulatory reporting requirements:
Create similar playbooks for other common incident types relevant to your organization, such as data exfiltration, supply chain compromise, DDoS attacks, and insider threats. Each playbook should include clear NIS2 reporting triggers and templates.
Regular exercises are essential to validate your NIS2 incident response capabilities:
| Exercise Type | Description | NIS2 Focus Areas | Frequency |
| Tabletop Exercises | Discussion-based scenarios with key stakeholders to validate decision-making | Reporting timelines, notification decisions, cross-border coordination | Quarterly |
| Technical Drills | Hands-on response activities for technical teams | Evidence collection, forensic preservation, technical documentation | Bi-monthly |
| Red Team / Blue Team | Simulated attacks to test detection and response capabilities | Time-to-detect, time-to-contain, evidence quality | Semi-annually |
| Full-Scale Simulations | Comprehensive scenarios involving all stakeholders and external parties | End-to-end response including regulatory reporting | Annually |
Exercises reveal process gaps. If a playbook can’t be executed under stress, it isn’t ready for a real incident or regulatory scrutiny.
Use realistic scenarios relevant to your organization, such as cloud service outages, managed service provider compromise, or ransomware affecting critical business functions. Measure outcomes including time-to-detect, time-to-contain, decision lag, and regulator notification readiness.
Register for our upcoming webinar: “NIS2 Tabletop Exercise Masterclass” to learn how to design and facilitate effective exercises that validate your regulatory compliance.
Effective communication is central to NIS2 compliance. Your communication plan should address three key audiences:
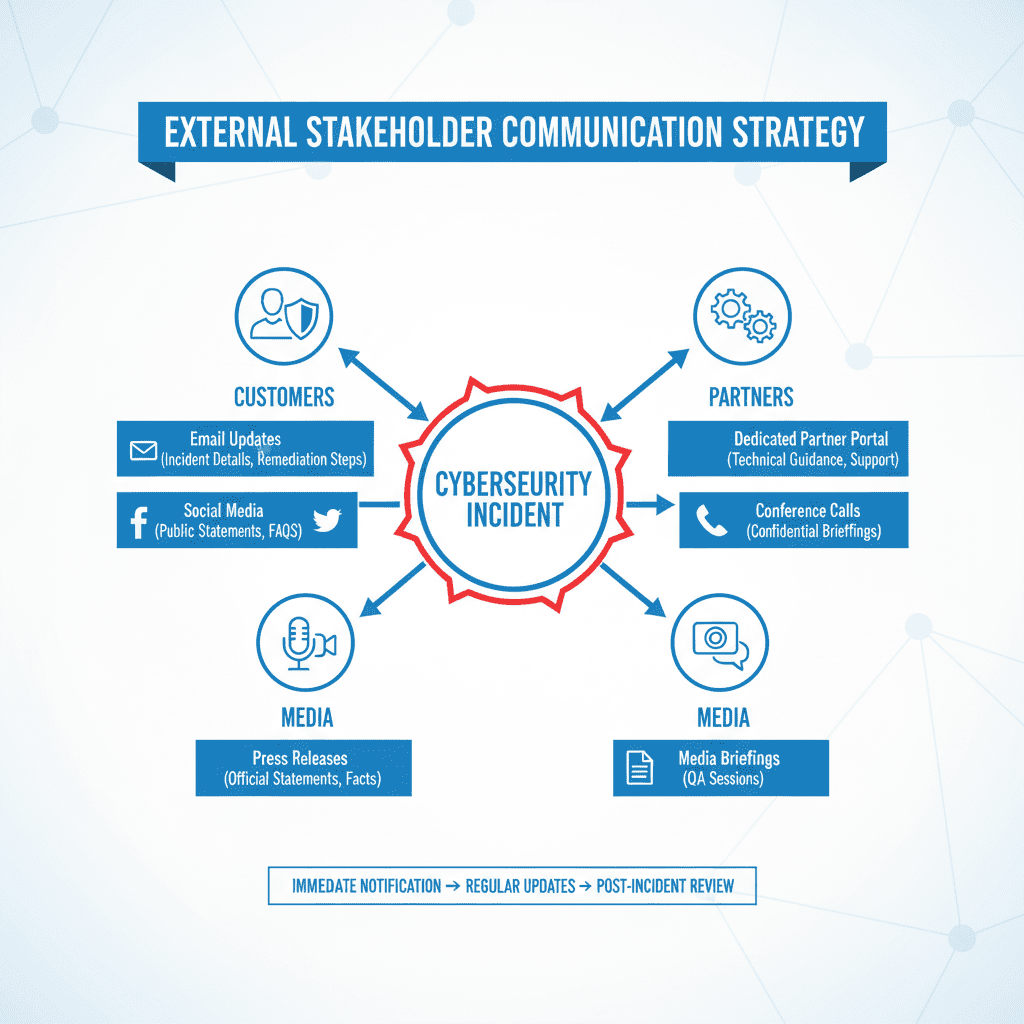
Include a communication matrix in every playbook that specifies who communicates what to whom, when, and through which channels. Ensure all external communications are reviewed by legal counsel to maintain accuracy while meeting regulatory obligations.
Early detection is critical for effective incident management and meeting NIS2 reporting timelines. Implement these key capabilities:
Implement comprehensive log collection and correlation with defined alerting thresholds. Ensure logs are preserved with appropriate retention periods to support forensic investigation and regulatory reporting.
Deploy EDR solutions across your environment to provide real-time visibility into endpoint activity, enable rapid containment actions, and collect forensic evidence required for NIS2 reporting.
Incorporate threat intelligence feeds relevant to your sector and geography to enhance detection capabilities. Focus on actionable intelligence that can be operationalized through detection rules and hunting activities.
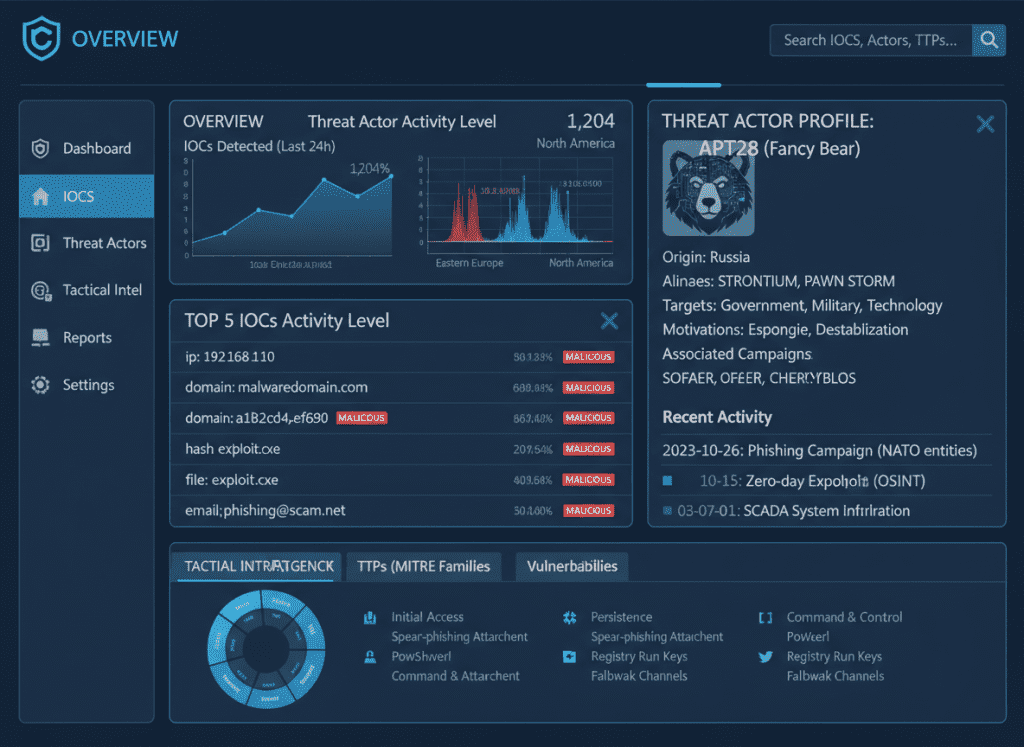
Implement user and entity behavior analytics (UEBA) to detect anomalous activity that might indicate compromise. This approach helps identify sophisticated attacks that might evade signature-based detection.
According to the IBM Cost of a Data Breach Report, organizations with mature detection capabilities reduce time-to-contain by an average of 74 days compared to those without such capabilities, which directly reduces remediation costs and regulatory exposure.
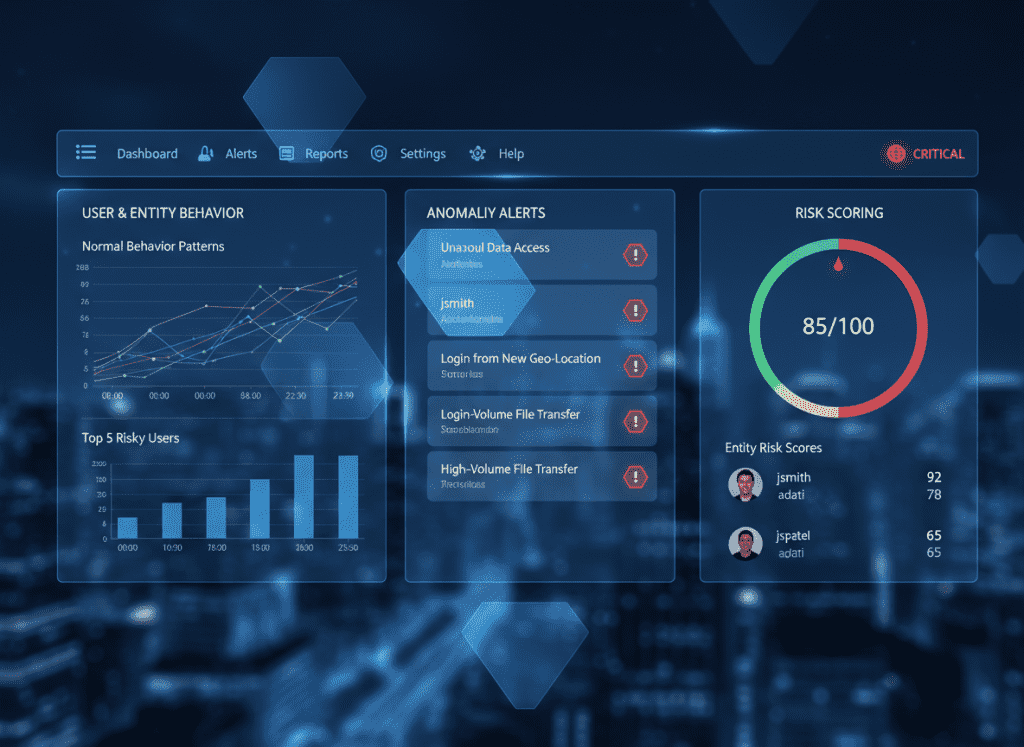
Effective triage ensures resources are allocated appropriately and NIS2 reporting obligations are identified quickly:
Implement a standardized incident classification system that aligns with NIS2 requirements:
| Severity Level | Criteria | Response Time | NIS2 Reporting |
| Critical | Significant impact on essential services, cross-border effects, substantial data breach | Immediate (24/7) | Required within 24 hours |
| High | Limited service disruption, potential for escalation, moderate data impact | Within 4 hours | Likely required (assess impact) |
| Medium | Minimal service impact, contained threat, limited data exposure | Within 8 hours | Possibly required (assess impact) |
| Low | No service impact, routine security event, no data exposure | Within 24 hours | Not typically required |
Use a standardized incident record template that captures all information needed for NIS2 reporting, including:
Download our NIS2-aligned Incident Triage Template to ensure consistent classification and timely reporting.
Effective containment minimizes incident impact while preserving evidence for regulatory reporting:
Implement micro-segmentation to limit lateral movement during incidents. Ensure containment actions are documented with timestamps to support NIS2 reporting requirements.
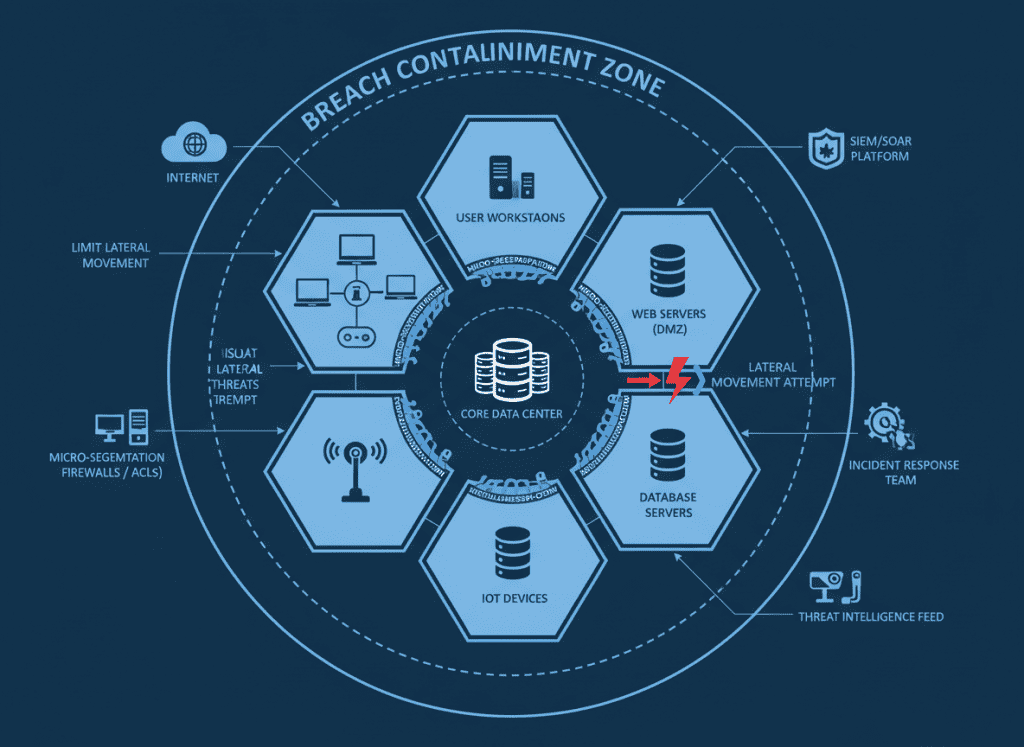
Develop “circuit breaker” capabilities to isolate compromised services while maintaining critical operations. Document service impact for NIS2 reporting on availability effects.
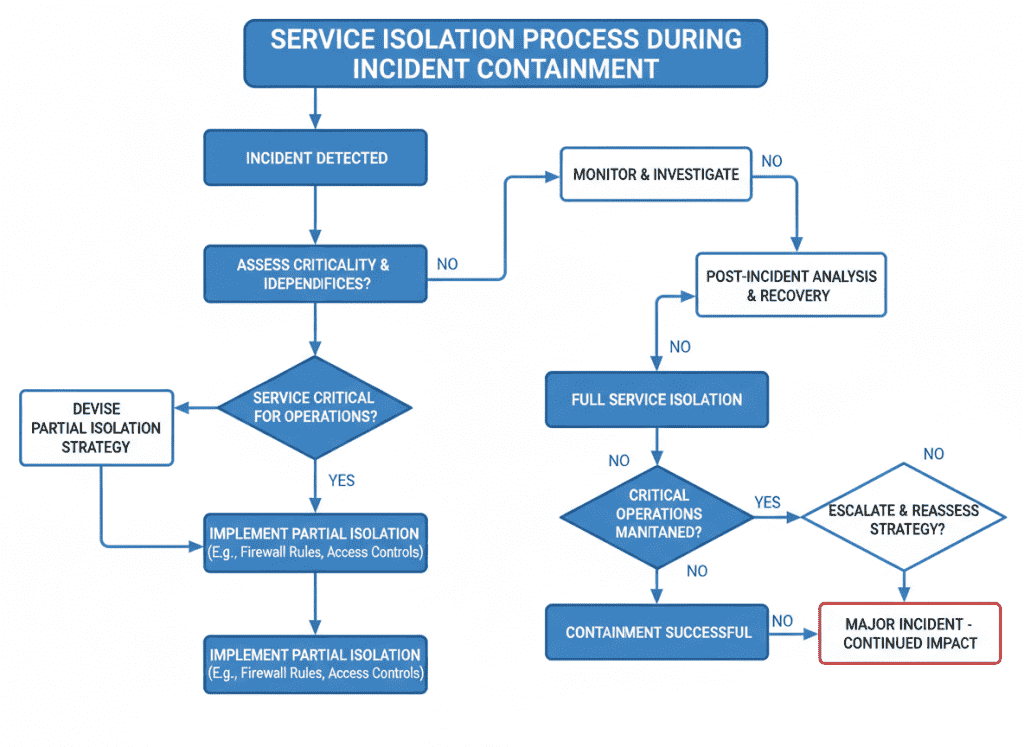
Implement forensic-first containment processes that preserve evidence before taking potentially destructive actions. This supports both investigation and regulatory reporting requirements.
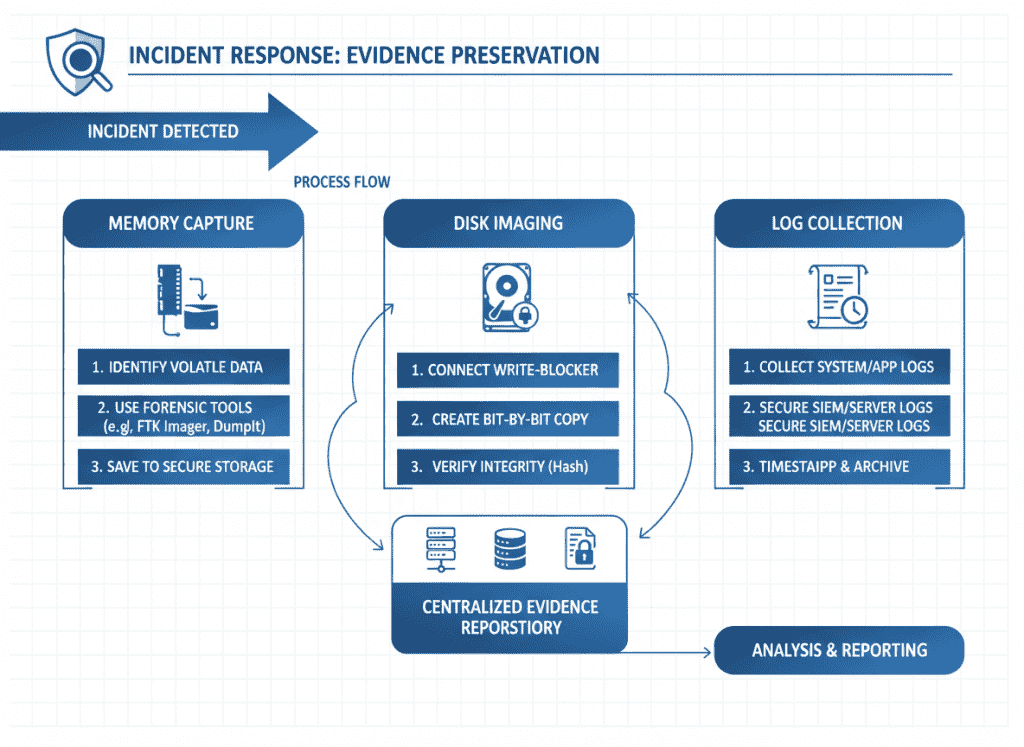
Maintain detailed records of all eradication activities, including malware removal, vulnerability patching, and security hardening. This documentation supports NIS2 reporting on remediation actions.
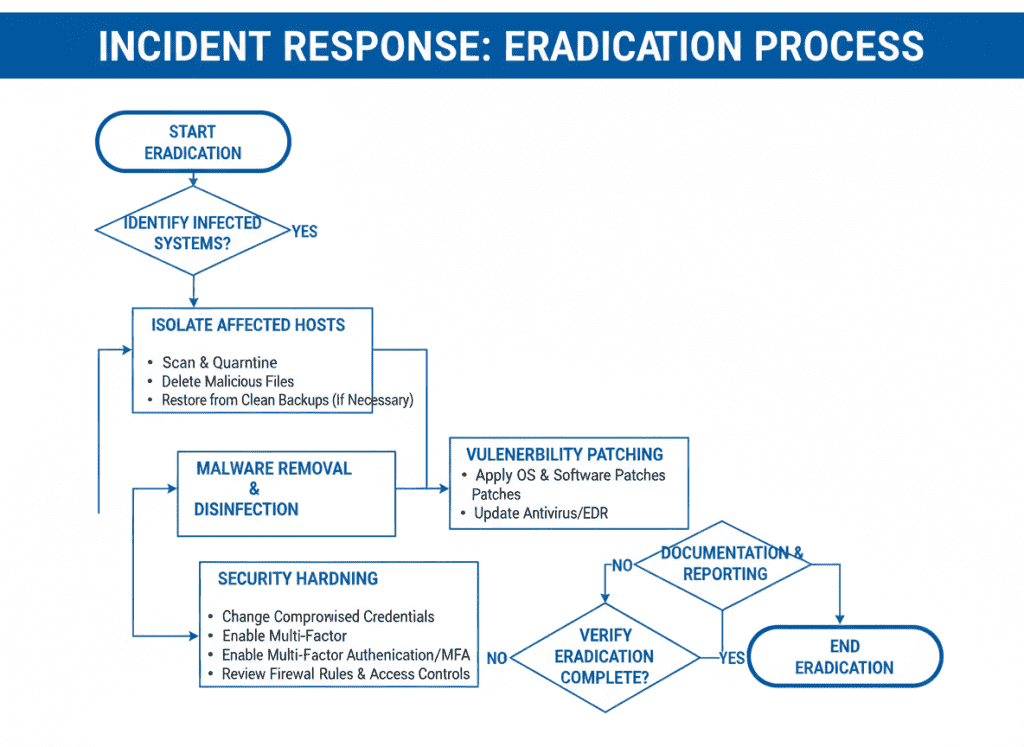
Always balance speed with evidence integrity during containment and eradication. Regulators will want to see what actions were taken, when they were performed, and their effectiveness in mitigating the incident.
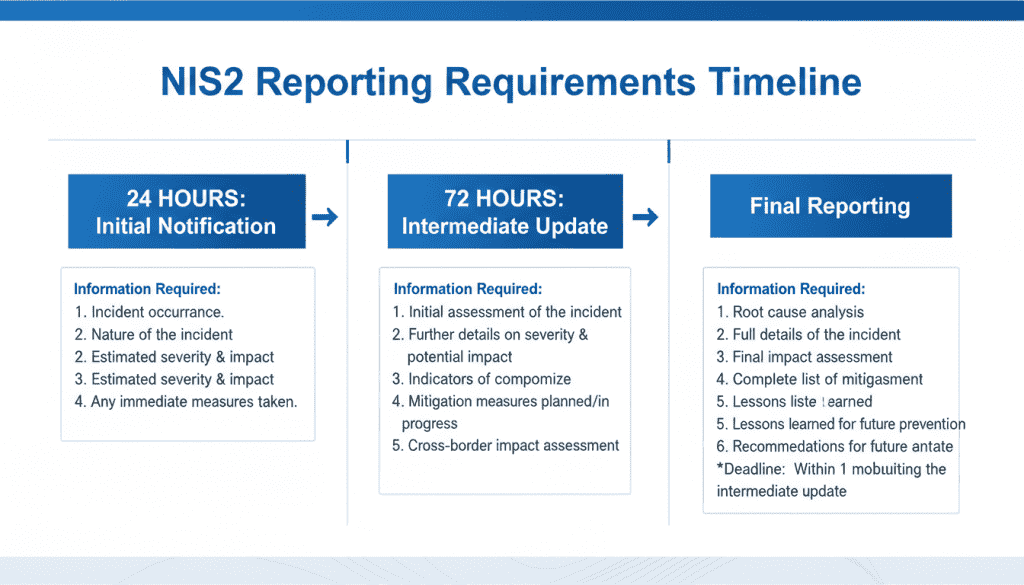
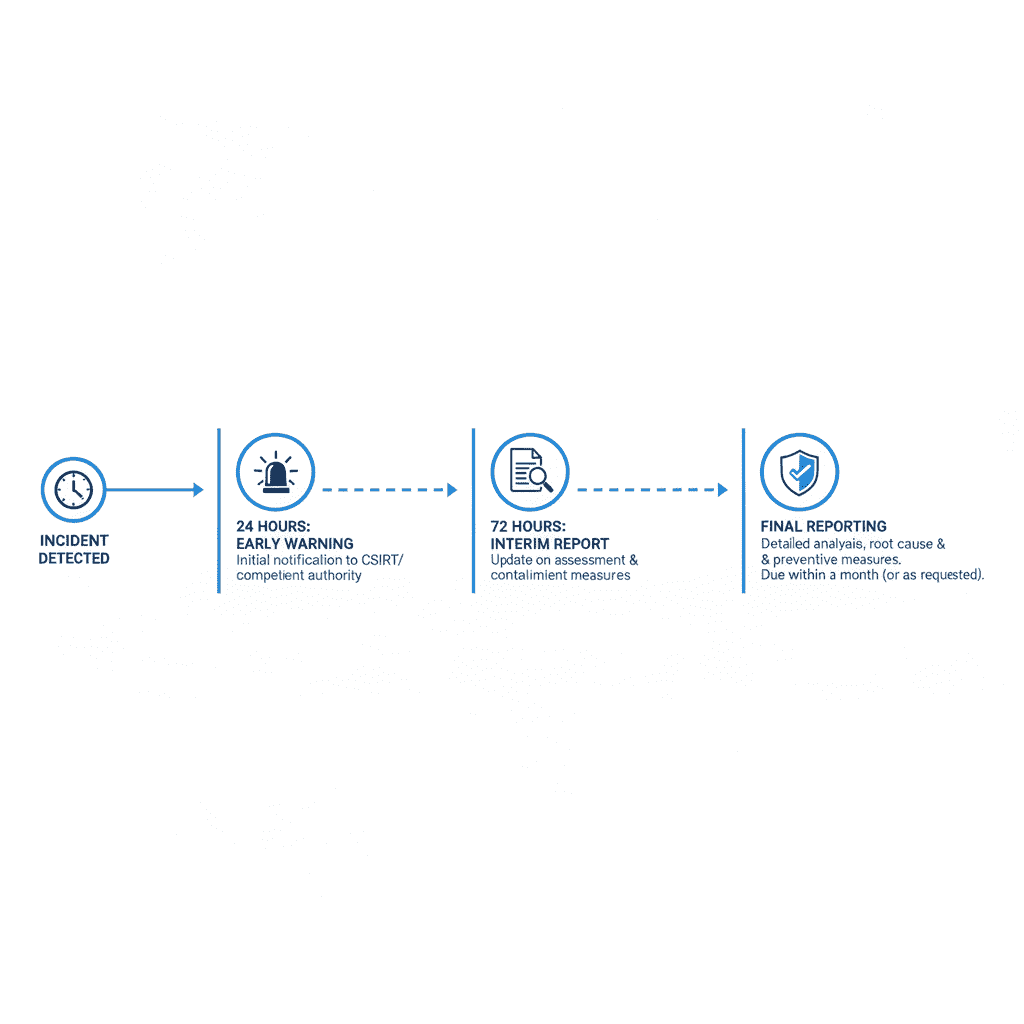
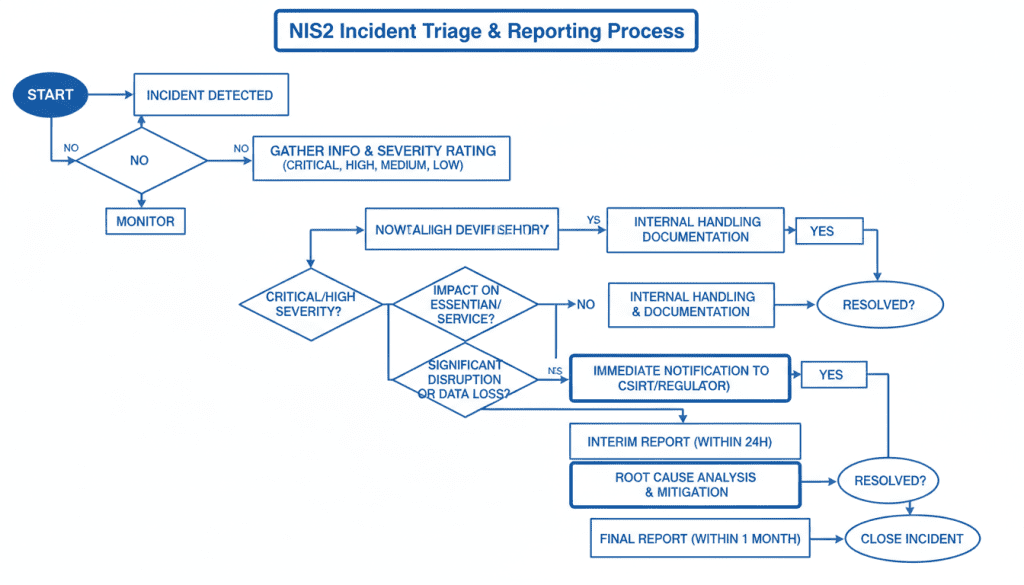
NIS2 establishes strict reporting obligations that organizations must follow:
| Reporting Stage | Timeline | Required Information | Recipients |
| Initial Notification | Within 24 hours of detection | Basic incident details, preliminary impact assessment, immediate containment actions | National CSIRT or competent authority |
| Progress Update | Within 72 hours of detection | Updated impact assessment, detailed technical information, ongoing response actions | National CSIRT or competent authority |
| Final Report | Within one month of resolution | Root cause analysis, complete impact assessment, remediation actions, lessons learned | National CSIRT or competent authority |
Important: Specific reporting timelines and thresholds may vary based on national implementation of NIS2. Check with your local regulatory authority for precise requirements in your jurisdiction.
Reporting obligations apply to incidents that have a significant impact on service provision or could have significant impact based on various factors, including:
For authoritative guidance, consult resources from ENISA and your national CSIRT or competent authority.
Comprehensive documentation is essential for regulatory compliance:
Maintain a detailed, tamper-evident timeline of all incident activities, including detection, containment, eradication, and recovery actions. Include timestamps, responsible parties, and outcomes.
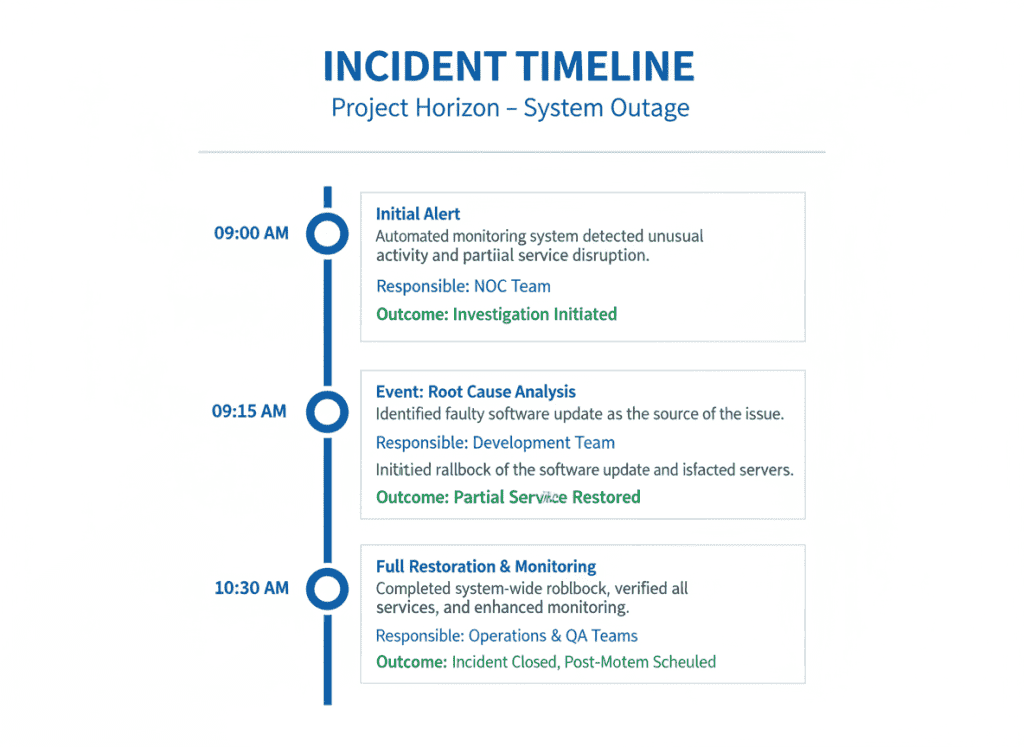
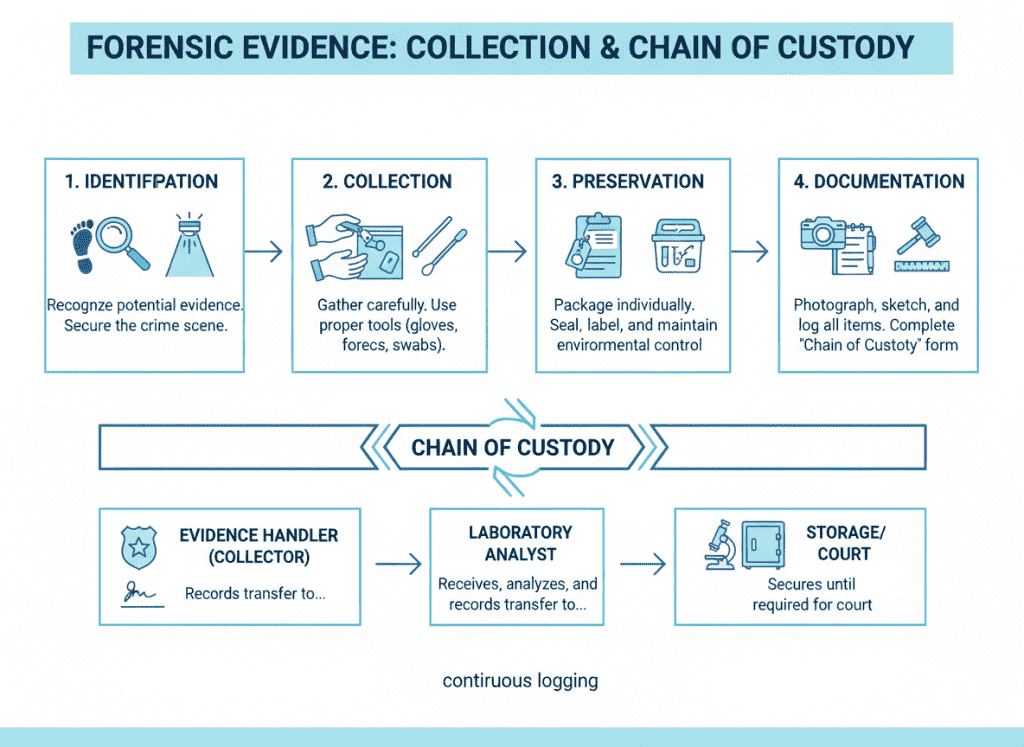
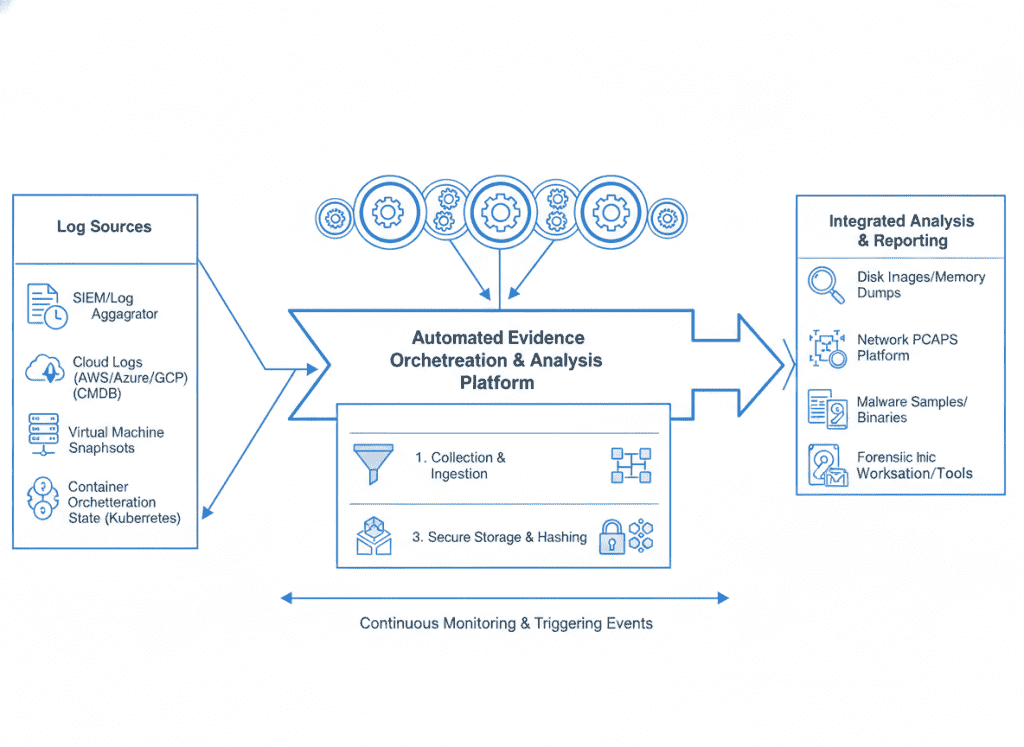
Preserve forensic evidence including disk images, memory dumps, network captures, and logs. Maintain chain of custody documentation for all evidence to ensure admissibility.
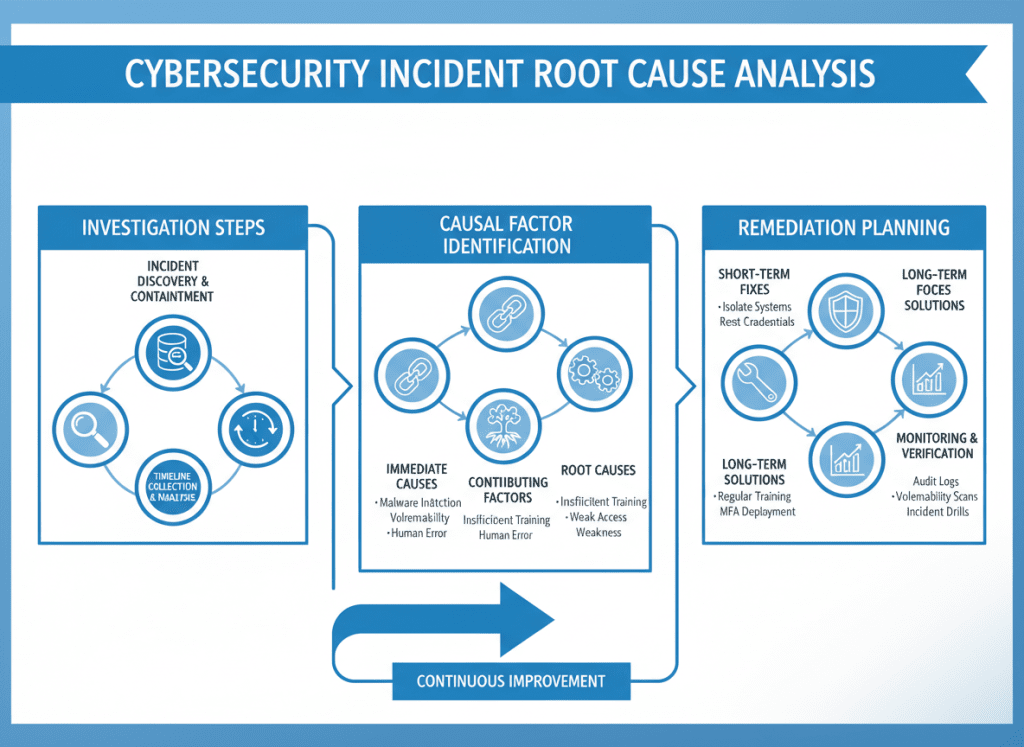
Conduct a formal root cause analysis that identifies the underlying vulnerabilities or weaknesses that enabled the incident. Include contributing factors and systemic issues.
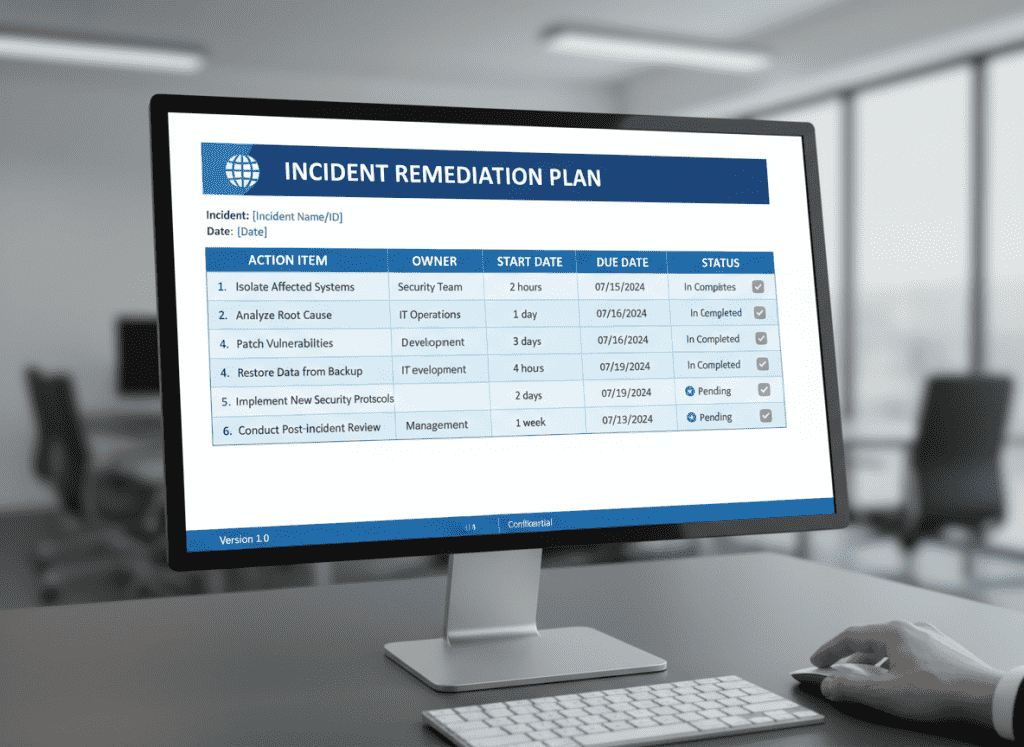
Develop a comprehensive remediation plan with specific actions, owners, and timelines. This demonstrates to regulators your commitment to addressing identified vulnerabilities.
Download our NIS2 Incident Documentation Package, including timeline templates, evidence collection checklists, and root cause analysis frameworks.
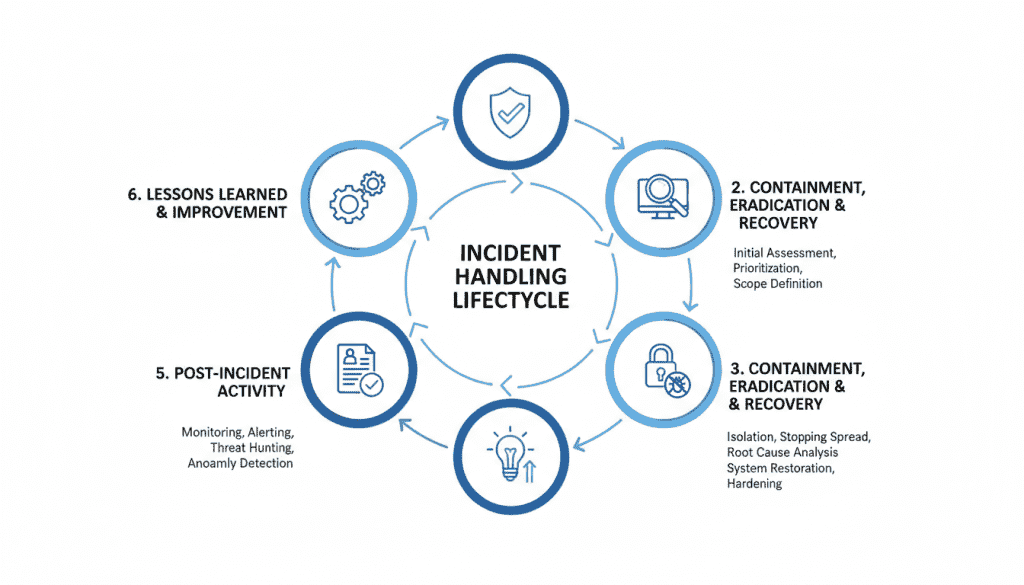
Post-incident activities are critical for demonstrating ongoing compliance and improving security posture:

A mature incident response program uses each NIS2 compliance incident as an opportunity to demonstrate improved resilience and regulatory commitment. Document all improvements and share them with leadership to demonstrate the value of your security investments.
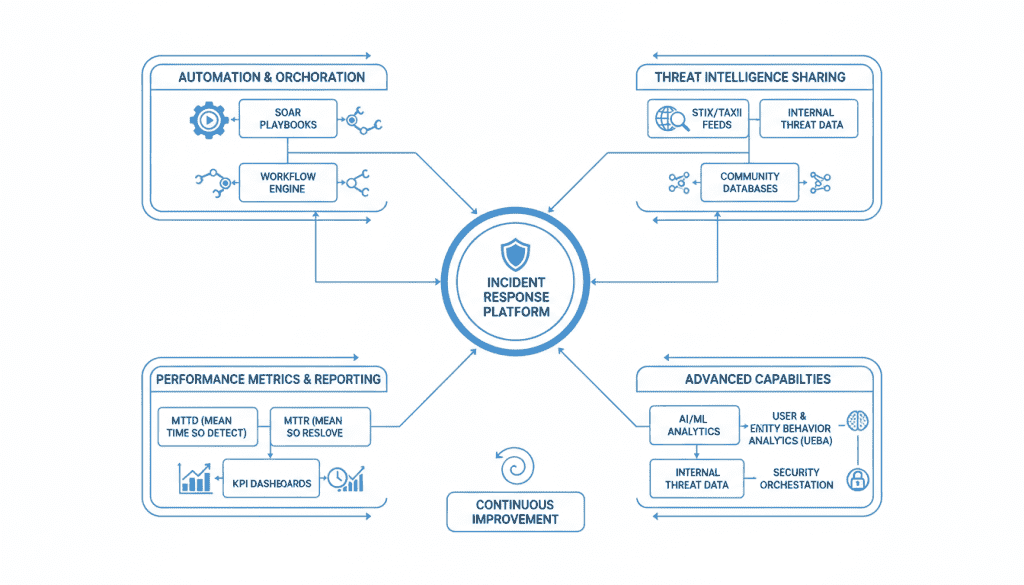
Security Orchestration, Automation and Response (SOAR) tools can significantly enhance your NIS2 incident management capabilities:
Implement automated collection of logs, system states, and forensic artifacts to ensure comprehensive evidence preservation while reducing manual effort.
Automate common response actions such as system isolation, credential resets, and indicator blocking to reduce response time and ensure consistency.
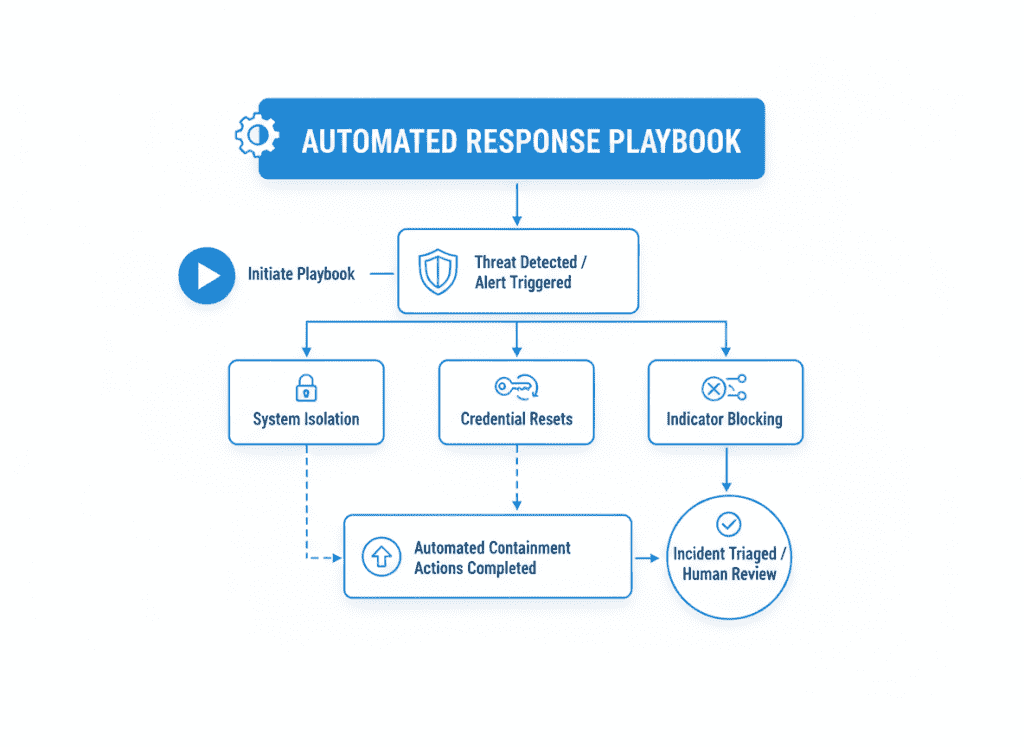
Implement automated workflows for NIS2 reporting that collect required information, generate notification templates, and track submission deadlines.

Integrate SOAR with SIEM, EDR, and ticketing systems to create a unified incident response platform with end-to-end traceability.
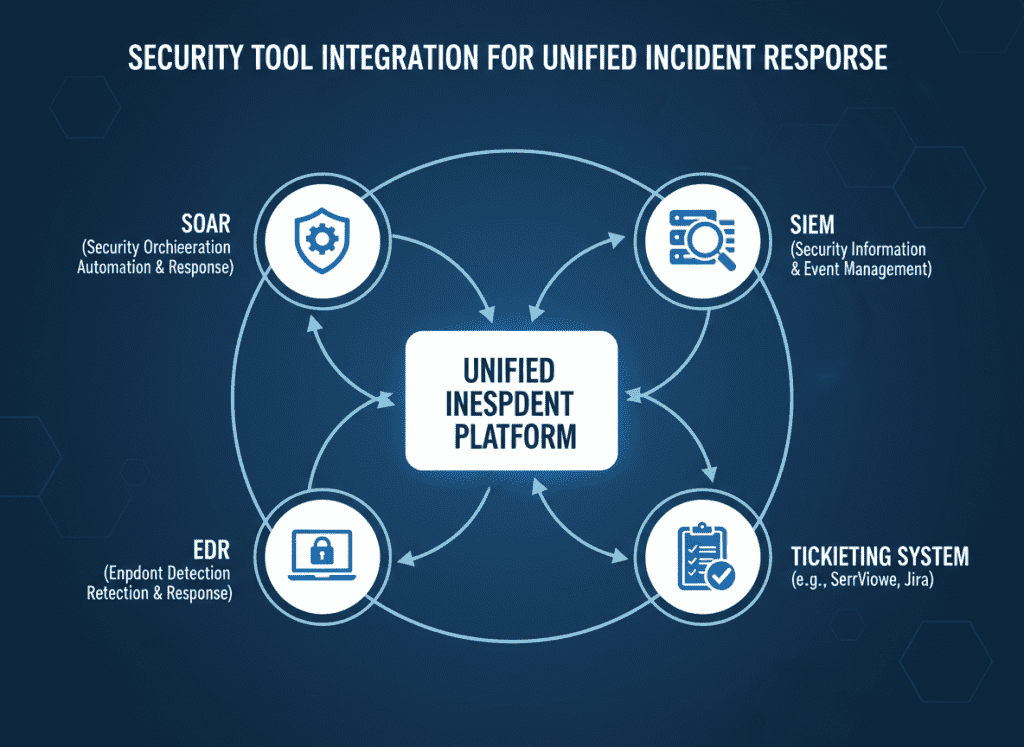
Automation reduces human error and improves time-to-notify, a critical metric under NIS2. It also ensures consistent execution of response procedures, even during high-stress incidents.
NIS2 encourages information sharing and cross-border cooperation to enhance collective resilience:


Schedule a consultation to learn how our threat intelligence services can strengthen your NIS2 incident response program.
Measuring incident response performance is essential for demonstrating compliance and driving improvement:
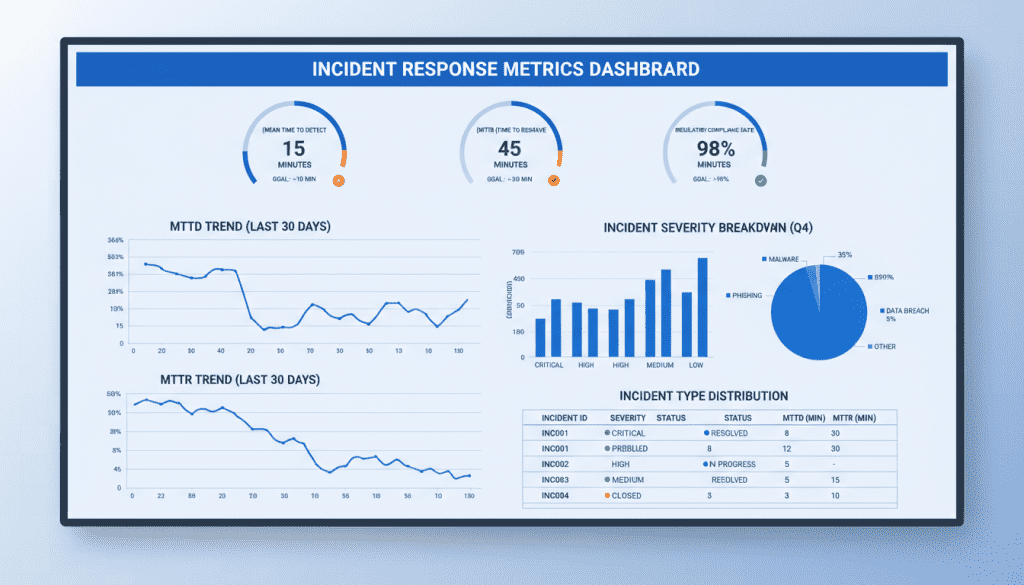
Key metrics to track for NIS2 compliance and program improvement include:
| Metric Category | Key Performance Indicators | NIS2 Relevance | Target |
| Detection Effectiveness | Mean Time to Detect (MTTD), detection source effectiveness, false positive rate | Earlier detection provides more time for analysis and reporting | MTTD |
| Response Efficiency | Mean Time to Respond (MTTR), containment effectiveness, time to recovery | Faster response reduces impact and reporting requirements | MTTR |
| Regulatory Compliance | Reporting timeline compliance, evidence quality, documentation completeness | Direct measure of regulatory obligations | 100% compliance |
| Continuous Improvement | Lessons implemented, recurring incident types, exercise findings addressed | Demonstrates ongoing risk reduction to regulators | 90% closure rate |
Create executive dashboards that translate technical metrics into business risk language. This helps leadership understand the value of your incident response program and supports resource allocation decisions.
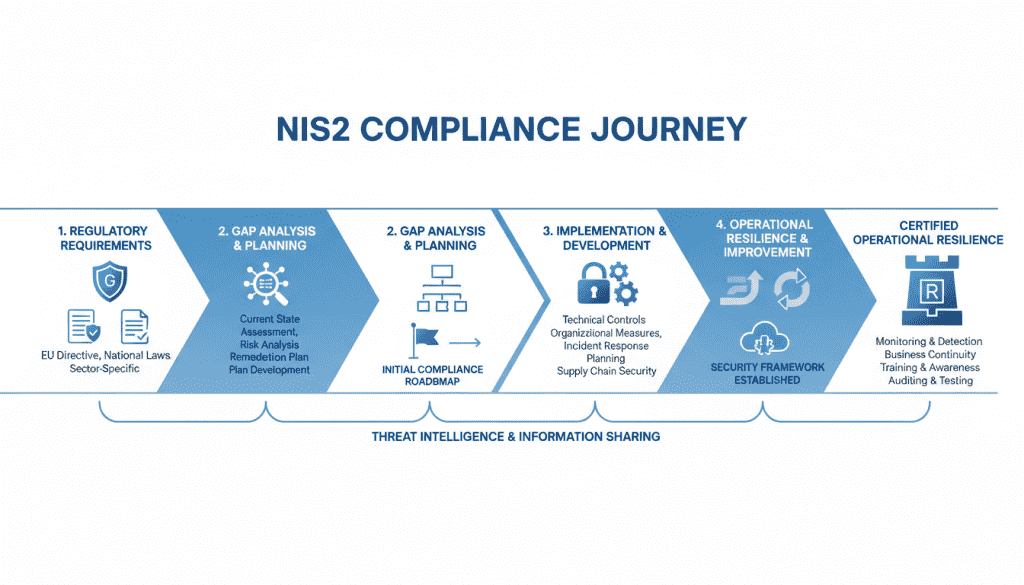
NIS2 incident management requires a comprehensive approach that integrates regulatory compliance with operational effectiveness:
To continue building your NIS2 incident management capabilities, consider these next steps:
Valuable resources for ongoing reference include:
Download our comprehensive NIS2 Incident Response Toolkit, including templates, playbooks, and implementation guides.
Experience power, efficiency, and rapid scaling with Cloud Platforms!