The NIS2 Directive represents a significant evolution in the European Union’s cybersecurity framework, expanding requirements across more sectors and introducing stricter enforcement mechanisms. For organizations operating in or serving EU markets, understanding this regulatory landscape is no longer optional—it’s a strategic imperative that affects operations, security posture, and compliance obligations.This guide breaks down the complex NIS2 compliance requirements into practical, actionable insights for security professionals, IT teams, and executive stakeholders. We’ll explore not just what the directive mandates, but how to implement it effectively within your organization’s existing security framework. Why NIS2 Matters Now
What NIS2 Is and Who It Affects
The Network and Information Systems Directive 2 (NIS2) is the European Union’s updated cybersecurity framework that significantly expands the scope of the original 2016 NIS Directive. It establishes common cybersecurity standards across Member States, requiring organizations to implement stronger risk management measures, report incidents promptly, and comply with minimum security requirements.
NIS2 applies to a much broader range of sectors than its predecessor, including:
Essential Entities
- Energy providers
- Transport operators
- Banking and financial institutions
- Healthcare organizations
- Drinking water suppliers
- Digital infrastructure providers
- Public administration
- Space industry operators
Important Entities
- Postal and courier services
- Waste management
- Chemical manufacturing
- Food production
- Digital service providers
- Research institutions
- Manufacturing of critical products
NIS2 raises the bar: broader coverage, stricter governance, and stronger reporting obligations for organizations across the European digital economy.
The Strategic Importance of the NIS2 Compliance Landscape
Understanding the NIS2 compliance landscape is now a strategic imperative, not just a regulatory checkbox. The directive introduces significant penalties for non-compliance—up to €10 million or 2% of global annual turnover for essential entities and up to €7 million or 1.4% of global annual turnover for important entities.
Beyond avoiding penalties, there are compelling business reasons to prioritize NIS2 compliance:
- Reduced operational risk: The IBM Cost of a Data Breach Report 2023 estimates the global average data breach cost at USD 4.45 million.
- Competitive advantage: Demonstrable compliance can be a market differentiator, especially when bidding for contracts with security-conscious clients.
- Operational resilience: The security measures required by NIS2 enhance overall business continuity and incident response capabilities.
- Supply chain relationships: As organizations scrutinize their vendors’ security postures, NIS2 compliance becomes a prerequisite for business partnerships.
How This Guide Addresses the Regulatory Requirements Overview
This practical guide will:
- Break down NIS2 regulations into digestible requirements and implementation timelines
- Present a practical NIS2 compliance framework with governance structures and technical controls
- Provide a methodology for conducting a compliance landscape analysis to assess your organization’s readiness
- Offer prioritized remediation planning based on risk and regulatory impact
- Recommend technology enablers and automation to streamline compliance efforts
- Address the operational impact on IT, security, and supply chain operations
NIS2 Regulations Explained: Core Requirements
Scope and Applicability of NIS2
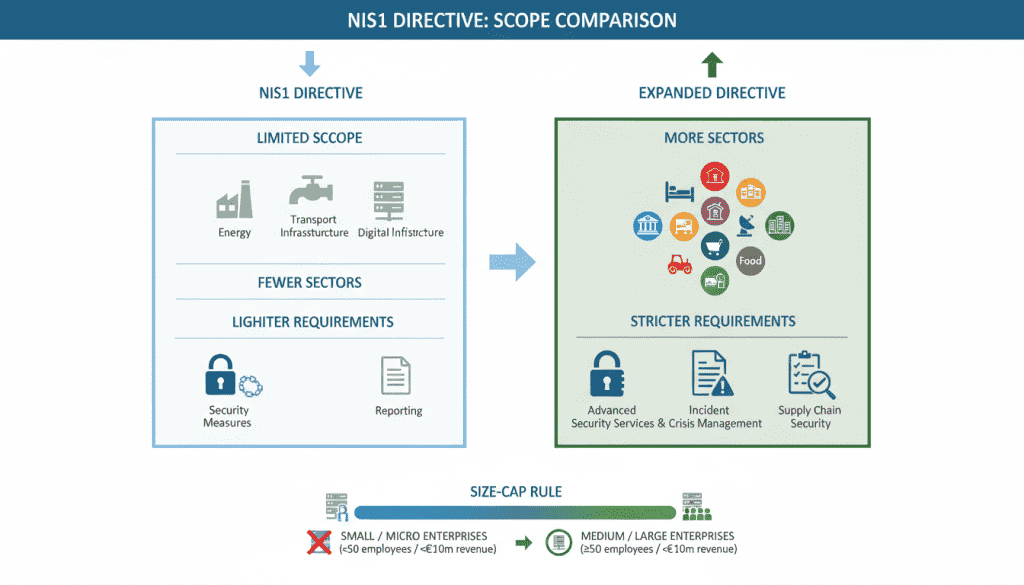
NIS2 significantly widens the regulatory net compared to the original NIS Directive. The key differences in scope include:
| Aspect | Original NIS Directive | NIS2 Directive |
| Sector Coverage | Limited to operators of essential services and digital service providers | Expanded to 18 sectors including manufacturing, waste management, food production, and more |
| Entity Classification | Member States identified operators of essential services | Size-cap rule automatically includes medium and large entities in covered sectors |
| Security Requirements | General security measures | More specific and comprehensive security measures with “all-hazards approach” |
| Incident Reporting | Notification of significant incidents | Strict reporting timelines (24 hours for early warning, 72 hours for incident notification) |
| Enforcement | Limited enforcement mechanisms | Significant penalties and personal liability for management |
A practical example: A medium-sized cloud service provider delivering hosting services across the EU would now be within scope of NIS2, requiring changes to contracts, security posture, and incident notification processes. Even if the company is headquartered outside the EU, it must designate an EU representative if it provides services to EU customers.
Key Regulatory Requirements Overview
The regulatory requirements overview for NIS2 centers on several key pillars:
1. Risk Management Measures
Organizations must implement appropriate and proportionate technical and organizational measures to manage risks to their network and information systems. These include:
- Policies on risk analysis and information system security
- Incident handling procedures
- Business continuity measures, including backup management and disaster recovery
- Supply chain security, covering relationships with direct suppliers and service providers
- Security in network and information systems acquisition and development
- Policies to assess the effectiveness of cybersecurity measures
- Basic cyber hygiene practices and cybersecurity training
- Cryptography and encryption policies
- Human resources security, access control, and asset management
- Multi-factor authentication and secure communications
2. Incident Reporting Obligations
NIS2 introduces strict incident reporting timelines:
- 24 hours: Early warning notification after becoming aware of a significant incident
- 72 hours: Incident notification with initial assessment of severity, impact, and indicators of compromise
- One month: Final report detailing root cause analysis and long-term remedial measures
3. Supply Chain Security
Organizations must address security risks in their supply chains by:
- Assessing the cybersecurity policies of suppliers and service providers
- Implementing appropriate security measures in contracts and agreements
- Evaluating supplier compliance with security requirements
- Maintaining an inventory of critical suppliers and their security posture
4. Governance and Accountability
NIS2 places direct responsibility on management bodies:
- Approval of cybersecurity risk management measures
- Supervision of implementation
- Mandatory cybersecurity training for management
- Personal liability for non-compliance
Legal Timelines and Enforcement Mechanisms
Understanding the legal timeline for NIS2 implementation is crucial for compliance planning:
- December 2022: NIS2 Directive (EU) 2022/2555 was published in the Official Journal of the European Union
- October 17, 2024: Deadline for Member States to transpose NIS2 into national law
- October 18, 2024: Application of national measures begins
- April 17, 2025: Member States must establish lists of essential and important entities
Enforcement mechanisms under NIS2 include:
- Supervisory powers: National authorities can conduct audits, request information, and issue binding instructions
- Financial penalties: Up to €10 million or 2% of global annual turnover for essential entities; up to €7 million or 1.4% for important entities
- Management liability: Temporary bans from management positions for serious non-compliance
- Corrective actions: Authorities can order remediation of identified deficiencies
Need Help Assessing Your NIS2 Compliance Status?
Download our comprehensive NIS2 Gap Analysis Template to quickly identify areas where your organization may need to strengthen its cybersecurity measures to meet compliance requirements.
Download Gap Analysis Template
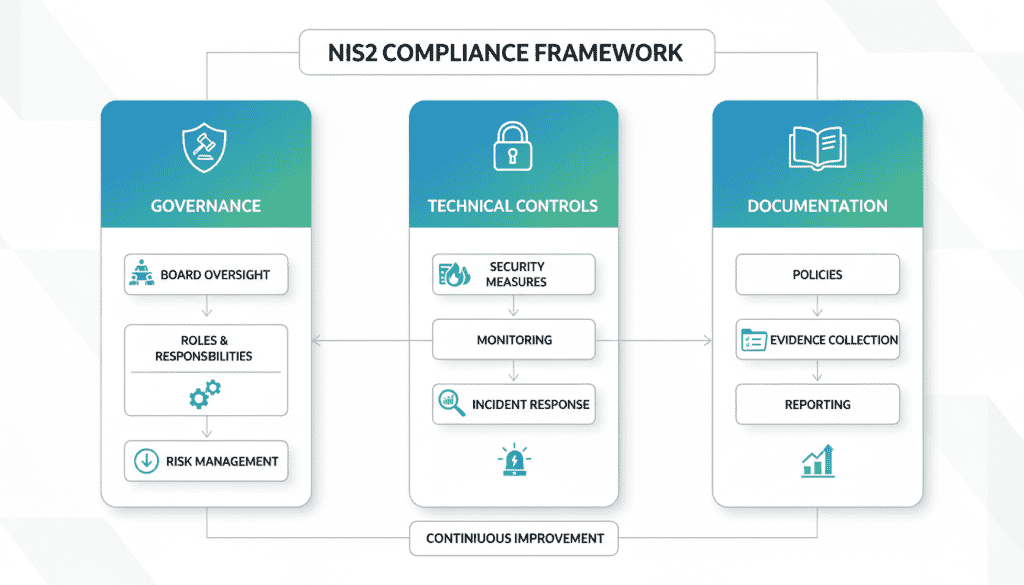
NIS2 Compliance Framework: Building Blocks for Organizations
Governance and Risk Management Structures
A robust NIS2 compliance framework starts with strong governance and clearly defined responsibilities:
Board-Level Accountability
Under NIS2, management bodies must take an active role in cybersecurity governance:
- Approve cybersecurity risk management measures
- Oversee implementation and effectiveness
- Receive regular briefings on the organization’s security posture
- Allocate adequate resources for cybersecurity
- Undergo cybersecurity training to understand risks and responsibilities
Designated Roles and Responsibilities
Establish clear roles to manage NIS2 compliance:
| Role | Responsibilities |
| Chief Information Security Officer (CISO) | Overall responsibility for cybersecurity strategy, implementation of security measures, and reporting to the board |
| Compliance Officer | Monitoring regulatory requirements, ensuring alignment with NIS2 obligations, and coordinating with national authorities |
| Incident Response Manager | Developing and testing incident response plans, coordinating response activities, and managing reporting obligations |
| Supply Chain Security Manager | Assessing supplier security, managing third-party risk, and ensuring contractual security requirements |
| IT/OT Security Leads | Implementing technical security controls, monitoring systems, and managing vulnerabilities |
Risk Management Program
Implement a structured risk management approach:
- Integrate cybersecurity risks into enterprise risk management
- Conduct regular risk assessments of network and information systems
- Maintain a risk register with identified risks, controls, and remediation plans
- Establish risk acceptance criteria and escalation procedures
- Review and update risk assessments following significant changes or incidents
Technical and Operational Controls
The technical foundation of the cybersecurity compliance landscape under NIS2 includes several key control areas:
Asset Management
Maintain comprehensive visibility of your technology landscape:
- Implement an authoritative inventory of hardware, software, and cloud services
- Classify assets based on criticality and sensitivity
- Document dependencies between systems and services
- Maintain up-to-date network diagrams and data flow maps
Identity and Access Management
Control access to systems and data:
- Implement the principle of least privilege
- Enforce multi-factor authentication for all users, especially for privileged accounts
- Establish strong password policies and regular credential rotation
- Implement privileged access management for administrative accounts
- Regularly review and audit access rights
Network and Endpoint Security
Protect your infrastructure from threats:
- Implement network segmentation to isolate critical systems
- Deploy next-generation firewalls and intrusion detection/prevention systems
- Use endpoint detection and response (EDR) solutions
- Encrypt sensitive data at rest and in transit
- Implement email and web filtering to block malicious content
Monitoring and Detection
Maintain visibility of security events:
- Implement a Security Information and Event Management (SIEM) system
- Establish 24/7 monitoring capabilities (internal or outsourced)
- Define alerting thresholds and escalation procedures
- Conduct regular threat hunting activities
- Monitor for unusual user behavior and potential data exfiltration
Incident Response
Prepare for security incidents:
- Develop and regularly test incident response plans
- Establish an incident response team with clearly defined roles
- Create communication templates for internal and external notifications
- Prepare reporting procedures aligned with NIS2 timelines
- Conduct regular tabletop exercises to test response capabilities
Business Continuity and Resilience
Ensure operational resilience:
- Implement regular, tested backup procedures
- Use immutable backups to protect against ransomware
- Develop disaster recovery plans with defined recovery time objectives
- Establish alternate processing sites for critical systems
- Test recovery procedures regularly
Documentation, Reporting, and Evidence Collection
NIS2 emphasizes the importance of documentation and evidence to demonstrate compliance:
Policy Documentation
Maintain comprehensive written policies:
- Information security policy
- Risk management framework
- Incident response procedures
- Business continuity and disaster recovery plans
- Access control and identity management policies
- Supply chain security requirements
- Acceptable use policies
Evidence Collection
Gather and retain evidence of security controls:
- Risk assessment reports and remediation plans
- Vulnerability scan results and patch management records
- Penetration test reports and remediation status
- Security awareness training records
- Access review documentation
- Incident response logs and post-incident reports
- Supplier security assessments
Reporting Templates
Prepare standardized reporting formats:
- Early warning notification template (24-hour requirement)
- Incident notification template (72-hour requirement)
- Final incident report template (one-month requirement)
- Executive dashboard for board reporting
- Regulatory compliance status reports
Tip: Keep a “regulatory pack” for each in-scope service that includes architecture diagrams, data flows, supplier lists, incident response playbooks, and proof of testing. This makes it easier to demonstrate compliance during audits or regulatory inquiries.
Streamline Your NIS2 Implementation
Download our 90-Day NIS2 Remediation Plan Template to prioritize your compliance efforts and create a structured roadmap for meeting key requirements.
Download 90-Day Plan Template
Compliance Landscape Analysis: Assessing Readiness and Gaps
Conducting a Gap Analysis Against NIS2 Regulations Explained
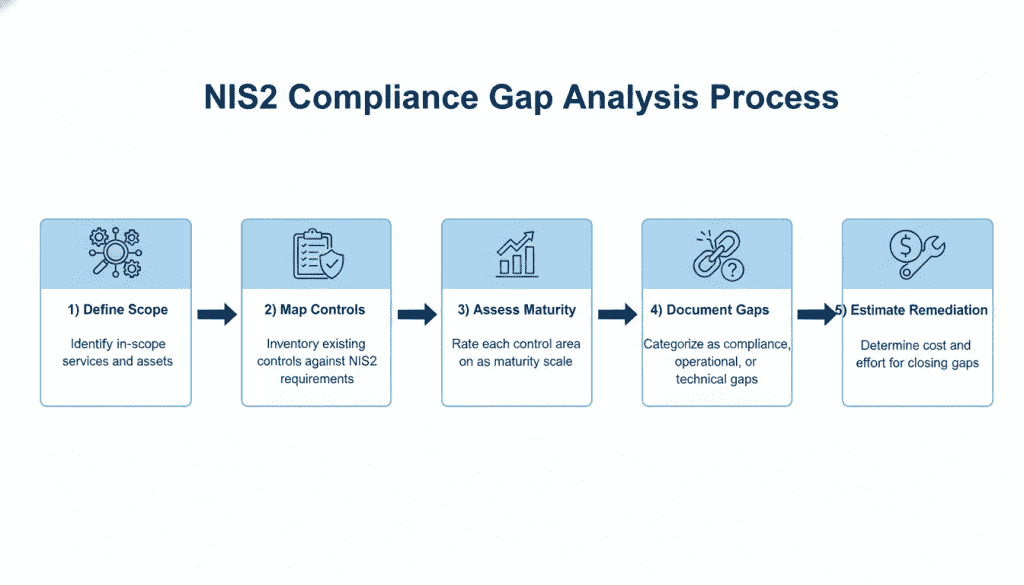
A methodical gap analysis is essential to understand your organization’s current compliance posture and identify areas requiring attention:
Step 1: Define Scope
Begin by identifying which parts of your organization fall under NIS2:
- Determine if your organization qualifies as an “essential” or “important” entity
- Identify which business units, services, and systems are in scope
- Document the critical network and information systems that support these services
- Map data flows and dependencies between systems
- Identify key suppliers and service providers that support in-scope services
Step 2: Map Controls
Inventory your existing security controls against NIS2 requirements:
- Create a comprehensive control framework based on NIS2 requirements
- Map existing controls to this framework
- Identify controls that are missing or inadequate
- Document the evidence available to demonstrate control effectiveness
Step 3: Assess Maturity
Evaluate the maturity of each control area using a consistent scale:
| Maturity Level | Description |
| 0 – Non-existent | Control is not implemented or planned |
| 1 – Initial | Control is ad hoc, disorganized, and reactive |
| 2 – Repeatable | Control is documented but not consistently applied |
| 3 – Defined | Control is well-documented, standardized, and consistently applied |
| 4 – Managed | Control is monitored, measured, and continuously improved |
| 5 – Optimized | Control is fully automated, integrated, and continuously optimized |
Step 4: Document Gaps
Categorize identified gaps for better remediation planning:
- Compliance gaps: Missing policies, procedures, or documentation
- Operational gaps: Inadequate processes, training, or awareness
- Technical gaps: Missing or insufficient security controls or technologies
- Governance gaps: Inadequate oversight, roles, or responsibilities
Step 5: Estimate Remediation
For each identified gap, assess:
- Required resources (budget, personnel, expertise)
- Estimated time to implement
- Dependencies on other initiatives or projects
- Potential challenges or constraints
Prioritization and Remediation Planning
Not all gaps are equal. Use a risk-based approach to prioritize remediation efforts:
Risk-Based Prioritization Factors
Consider these factors when prioritizing gaps:
- Regulatory impact: How critical is this requirement for NIS2 compliance?
- Security impact: How significant is the security risk if this gap remains?
- Operational impact: How would a security incident affect critical services?
- Implementation complexity: How difficult is it to address this gap?
- Resource requirements: What budget and personnel are needed?
- Dependencies: Are there prerequisites or dependencies to consider?
Remediation Roadmap
Develop a phased approach to remediation:
Phase 1: Quick Wins (0-3 months)
- Implement multi-factor authentication
- Develop incident response procedures
- Create reporting templates
- Conduct initial security awareness training
- Implement critical security patches
Phase 2: Medium-Term (3-9 months)
- Enhance monitoring and detection capabilities
- Implement network segmentation
- Develop supplier security assessment process
- Enhance backup and recovery capabilities
- Conduct penetration testing
Phase 3: Long-Term (9-18 months)
- Implement advanced security technologies
- Automate security processes
- Enhance security metrics and reporting
- Develop continuous improvement program
- Conduct comprehensive security assessments
Measuring Maturity Within the NIS2 Compliance Landscape
Track your progress with measurable key performance indicators (KPIs):
Security Posture Metrics
- Percentage of assets with up-to-date security patches
- Percentage of users with multi-factor authentication enabled
- Number of critical vulnerabilities and average time to remediate
- Percentage of systems with security monitoring enabled
- Percentage of privileged accounts with enhanced controls
Operational Metrics
- Mean time to detect (MTTD) security incidents
- Mean time to respond (MTTR) to security incidents
- Percentage of incidents reported within required timeframes
- Number of security incidents by category
- Percentage of staff who have completed security awareness training
Compliance Metrics
- Overall NIS2 compliance score by control area
- Percentage of identified gaps remediated
- Number of open audit findings and average time to close
- Percentage of suppliers assessed for security compliance
- Number of policy exceptions and compensating controls
Accelerate Your NIS2 Implementation with ISO 27001
Already ISO 27001 certified? Download our ISO 27001 to NIS2 Control Mapping to leverage your existing security framework and fast-track your compliance efforts.
Download ISO 27001 Mapping
NIS2 Compliance Impact: Operational and Business Considerations
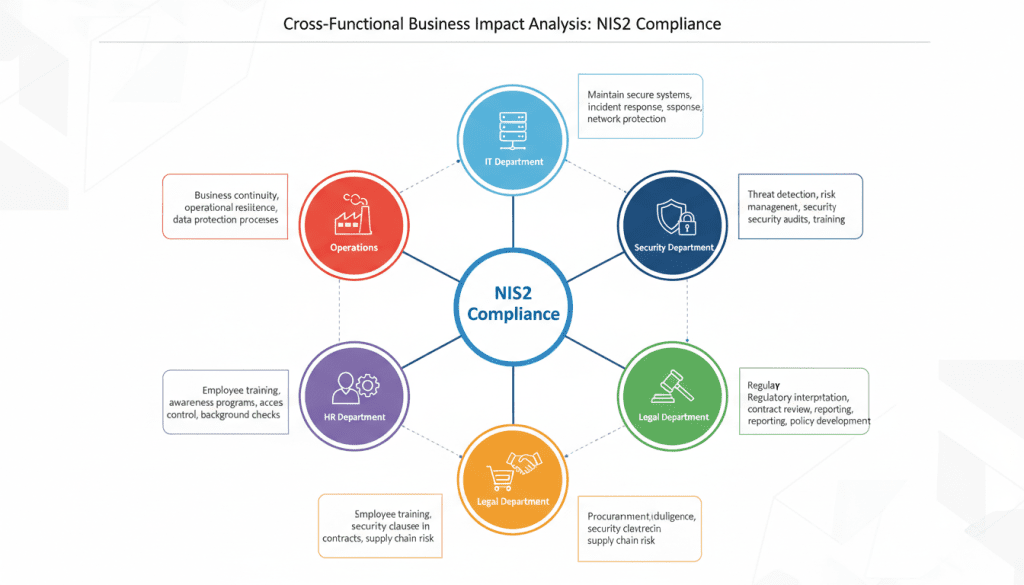
Impact on IT, Security, and Supply Chain Operations
Implementing NIS2 compliance will have significant operational implications across multiple business functions:
IT Department Impact
The IT function will bear significant responsibility for implementing technical controls:
- Increased logging and monitoring requirements
- Enhanced access control and authentication mechanisms
- More rigorous change management processes
- Expanded backup and recovery capabilities
- More frequent security patching and updates
- Enhanced network segmentation and protection
Security Team Impact
Security teams will need to expand their capabilities:
- 24/7 monitoring and incident response capabilities
- Enhanced threat intelligence and analysis
- More frequent security testing and assessments
- Development of comprehensive security metrics
- Expanded security awareness and training programs
- More rigorous vulnerability management
Supply Chain Impact
NIS2’s supply chain security requirements will affect procurement and vendor management:
- Enhanced supplier security assessment processes
- New contractual clauses for security requirements
- Regular monitoring of supplier compliance
- More rigorous onboarding and offboarding procedures
- Contingency planning for supplier disruptions
Example: A managed service provider must now revise all customer contracts to include incident notification commitments and ensure that subcontractors meet minimum security measures. This requires updating contract templates, conducting security assessments of all subcontractors, and implementing new monitoring capabilities to detect and report incidents within required timeframes.
Legal and Compliance Impact
Legal and compliance functions will need to adapt:
- Development of new policies and procedures
- Enhanced documentation and evidence collection
- Coordination with national competent authorities
- Management of regulatory reporting obligations
- Alignment with other regulatory requirements (e.g., GDPR)
Cost, Resource, and Timeline Implications
Organizations should prepare for significant investments in NIS2 compliance:
Budget Considerations
Compliance costs will vary based on organization size, complexity, and current maturity:
- Small organizations: €50,000 – €150,000 for initial compliance
- Medium organizations: €150,000 – €500,000 for comprehensive implementation
- Large organizations: €500,000 – €2,000,000+ for enterprise-wide compliance
These costs typically include:
- Technology investments (security tools, monitoring systems)
- External consulting and assessment services
- Staff training and awareness programs
- Documentation and policy development
- Ongoing compliance management
Resource Requirements
NIS2 compliance will require dedicated personnel:
- Security specialists for implementation and operation
- Compliance professionals for documentation and reporting
- IT staff for technical control implementation
- Legal expertise for contractual and regulatory matters
- Project management for coordination and tracking
Many organizations will need to increase security headcount or outsource certain functions, such as:
- Managed Detection and Response (MDR) services
- Security Operations Center (SOC) capabilities
- Penetration testing and vulnerability assessment
- Compliance advisory services
Implementation Timelines
Realistic timeframes for achieving NIS2 compliance:
- Initial assessment and planning: 1-3 months
- Policy and procedure development: 2-4 months
- Technical control implementation: 6-12 months
- Testing and validation: 2-3 months
- Full compliance maturity: 12-24 months
According to the European Union Agency for Cybersecurity (ENISA), organizations that proactively invest in cybersecurity measures spend an average of 9% of their IT budget on security, representing a significant increase of 1.9 percentage points from 2022. This trend reflects the growing recognition of cybersecurity as a strategic priority.
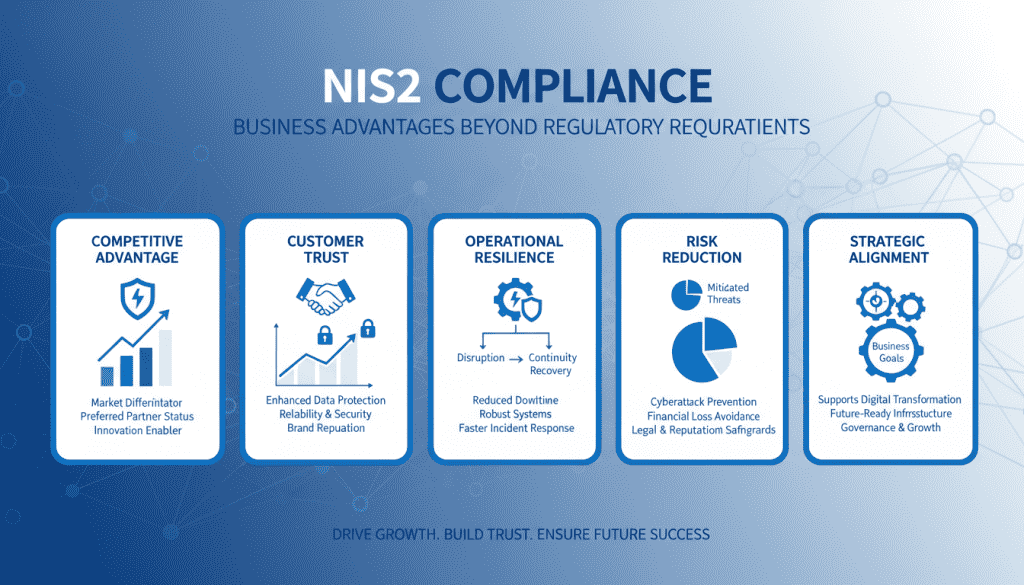
Strategic Benefits Beyond Compliance
While NIS2 compliance requires significant investment, it also offers strategic advantages:
Operational Benefits
- Enhanced resilience: Reduced downtime and faster recovery from incidents
- Improved visibility: Better understanding of assets, risks, and security posture
- Operational efficiency: Streamlined security processes and automation
- Reduced incident costs: Lower impact and faster resolution of security events
- Better decision-making: Data-driven security investments based on risk
Business Benefits
- Competitive advantage: Demonstrable security practices as a market differentiator
- Customer trust: Enhanced reputation for security and reliability
- Market access: Qualification for contracts requiring regulatory compliance
- Reduced liability: Lower risk of regulatory penalties and legal action
- Strategic alignment: Security integrated into business strategy and operations
Implementation Best Practices and Tools
Creating an Actionable NIS2 Compliance Framework
A practical NIS2 compliance framework should integrate with existing security programs while addressing specific regulatory requirements:
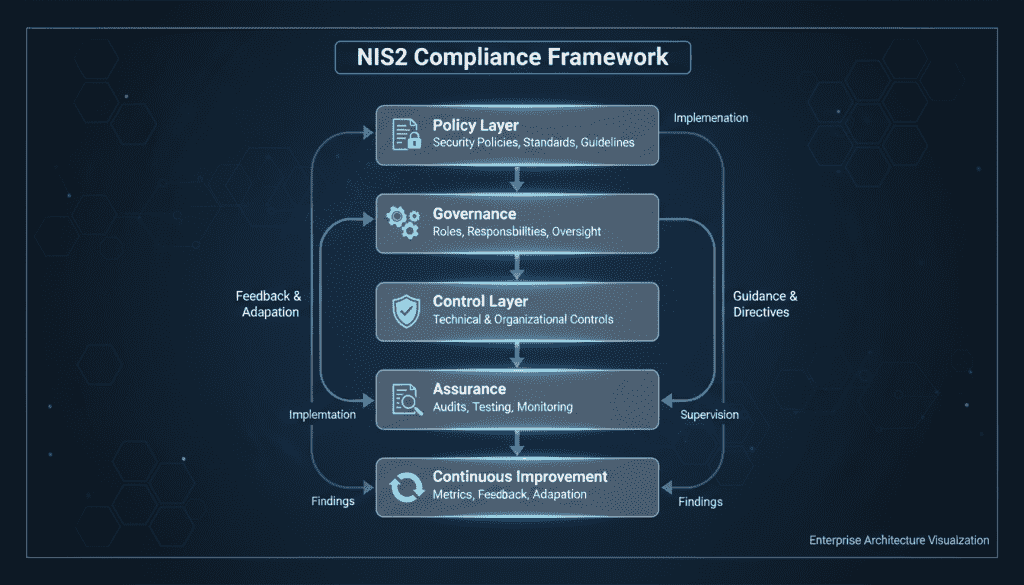
Framework Components
A comprehensive framework should include:
- Policy layer: Security policies, data protection standards, incident handling procedures
- Governance layer: Roles, responsibilities, reporting structures, oversight mechanisms
- Control layer: Technical and organizational controls mapped to NIS2 requirements
- Assurance layer: Audits, assessments, testing, and monitoring activities
- Continuous improvement: Metrics, feedback loops, and adaptation processes
Leveraging Existing Frameworks
Accelerate implementation by building on established security frameworks:
| Framework | Relevance to NIS2 | Implementation Advantage |
| ISO/IEC 27001 | Covers approximately 70% of NIS2 requirements | Provides a structured approach to information security management with certification option |
| NIST Cybersecurity Framework | Aligns well with NIS2’s risk-based approach | Offers flexible implementation guidance with Identify, Protect, Detect, Respond, Recover functions |
| CIS Controls | Provides practical, prioritized security controls | Offers implementation guidance by organization size and maturity level |
| COBIT | Addresses governance aspects of NIS2 | Strong focus on IT governance, risk management, and compliance |
Integration with Other Compliance Requirements
Harmonize NIS2 compliance with other regulatory obligations:
- GDPR: Align data protection measures and incident reporting
- DORA: Leverage overlapping requirements for financial sector entities
- eIDAS: Integrate with trust service provider requirements
- Sector-specific regulations: Incorporate industry-specific security requirements
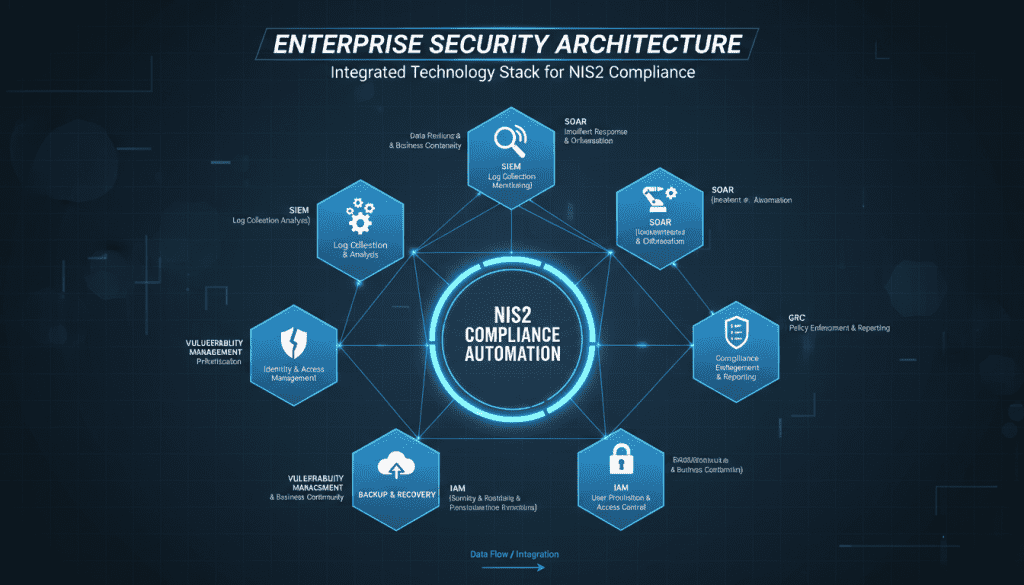
Technology Enablers and Automation
The right technology stack can significantly streamline NIS2 compliance efforts:
Security Information and Event Management (SIEM)
SIEM solutions provide critical capabilities for NIS2 compliance:
- Centralized log collection and correlation
- Real-time monitoring and alerting
- Incident detection and investigation
- Compliance reporting and evidence collection
- Threat intelligence integration
Security Orchestration, Automation, and Response (SOAR)
SOAR platforms enhance incident management:
- Automated incident response workflows
- Standardized investigation procedures
- Integration with security tools and systems
- Automated reporting to meet NIS2 timelines
- Case management and documentation
Governance, Risk, and Compliance (GRC) Platforms
GRC tools streamline compliance management:
- Centralized policy and control management
- Automated compliance assessments
- Risk register and remediation tracking
- Evidence collection and audit support
- Compliance reporting and dashboards
Identity and Access Management (IAM)
IAM solutions support access control requirements:
- Centralized user management
- Multi-factor authentication
- Privileged access management
- Access certification and review
- Single sign-on and directory integration
Vulnerability and Patch Management
These tools help maintain secure systems:
- Automated vulnerability scanning
- Prioritized remediation guidance
- Patch deployment and verification
- Compliance reporting
- Risk-based vulnerability management
Engaging Stakeholders and External Partners
Successful NIS2 implementation requires effective collaboration across multiple stakeholders:
Internal Stakeholder Engagement
Ensure alignment across the organization:
- Executive leadership: Secure support, resources, and strategic alignment
- IT and security teams: Drive technical implementation and operations
- Legal and compliance: Ensure regulatory interpretation and alignment
- Procurement: Update supplier requirements and contracts
- Business units: Identify critical services and operational requirements
- Human resources: Support training and awareness programs
External Partner Collaboration
Leverage external expertise and support:
- Consultants and advisors: Provide specialized expertise and implementation support
- Technology vendors: Offer solutions and implementation assistance
- Managed service providers: Deliver ongoing security operations and monitoring
- Legal counsel: Provide regulatory interpretation and contractual guidance
- Auditors and assessors: Validate compliance and identify improvement areas
Supplier and Third-Party Management
Ensure supply chain security:
- Develop security requirements for suppliers
- Update contracts with security and incident reporting obligations
- Implement supplier assessment and monitoring processes
- Establish incident coordination procedures with key suppliers
- Verify supplier compliance through assessments and audits
Best practice: Run cross-functional tabletop exercises to align stakeholders on incident roles, regulatory notification requirements, and customer communication procedures. These exercises help identify gaps in coordination and communication before a real incident occurs.
Conclusion: Next Steps and Resources
Executive Checklist for Immediate Actions
Take these steps now to prepare for NIS2 compliance:
- Determine applicability: Assess whether your organization qualifies as an “essential” or “important” entity under NIS2
- Conduct a gap analysis: Map your current security controls against NIS2 requirements
- Appoint responsible leadership: Designate a senior accountable person for NIS2 compliance
- Implement quick wins: Focus on high-impact, low-effort improvements like multi-factor authentication and patch management
- Develop incident reporting procedures: Create templates and processes to meet NIS2 reporting timelines
- Review supplier contracts: Update agreements to include security requirements and incident reporting obligations
- Initiate awareness training: Ensure staff understand NIS2 requirements and their responsibilities
Long-Term Compliance Governance Recommendations
Establish sustainable compliance practices:
- Integrate with enterprise risk management: Embed cybersecurity risks into your organization’s overall risk framework
- Implement continuous monitoring: Deploy technologies and processes for ongoing security assessment
- Establish regular review cycles: Conduct periodic assessments of security controls and compliance status
- Develop compliance metrics: Create KPIs to track and report on compliance maturity
- Conduct regular testing: Perform penetration tests, tabletop exercises, and security assessments
- Maintain documentation: Keep policies, procedures, and evidence up to date
- Stay informed: Monitor regulatory developments and update your compliance program accordingly
Resources, Templates, and Further Reading
Leverage these resources to support your NIS2 compliance journey:
Official Resources
Implementation Guidance
Final practical takeaway: Treat NIS2 as a strategic program combining legal, technical, and operational change. Start with scope and gap analysis, prioritize by risk, and build an auditable NIS2 compliance framework that scales with your organization.
Ready to Start Your NIS2 Compliance Journey?
Contact your CISO or compliance lead to begin the scoping exercise this week. Early action is the best defense against both cyber risk and regulatory exposure.
If you’d like additional support, we can provide:
- A downloadable gap analysis template mapped to NIS2 controls
- A 90-day remediation plan tailored to your sector
- ISO/IEC 27001 to NIS2 requirements mapping for accelerated implementation
Request NIS2 Resources