
Cybersecurity Cost-Benefit Analysis: A Framework for Strategic Investment
January 13, 2026|2:37 PM
Unlock Your Digital Potential
Whether it’s IT operations, cloud migration, or AI-driven innovation – let’s explore how we can support your success.

January 13, 2026|2:37 PM
Whether it’s IT operations, cloud migration, or AI-driven innovation – let’s explore how we can support your success.
In today’s digital landscape, cybersecurity investments are no longer optional—they’re essential. Yet many organizations struggle to quantify the return on these investments, making it difficult to secure budget approval and prioritize security initiatives. A robust cybersecurity cost-benefit analysis provides the framework needed to make informed decisions, justify spending to stakeholders, and ensure your security budget delivers maximum value. This guide will walk you through the process of evaluating cybersecurity investments through a financial lens, helping you build a compelling business case for protecting your most valuable digital assets.
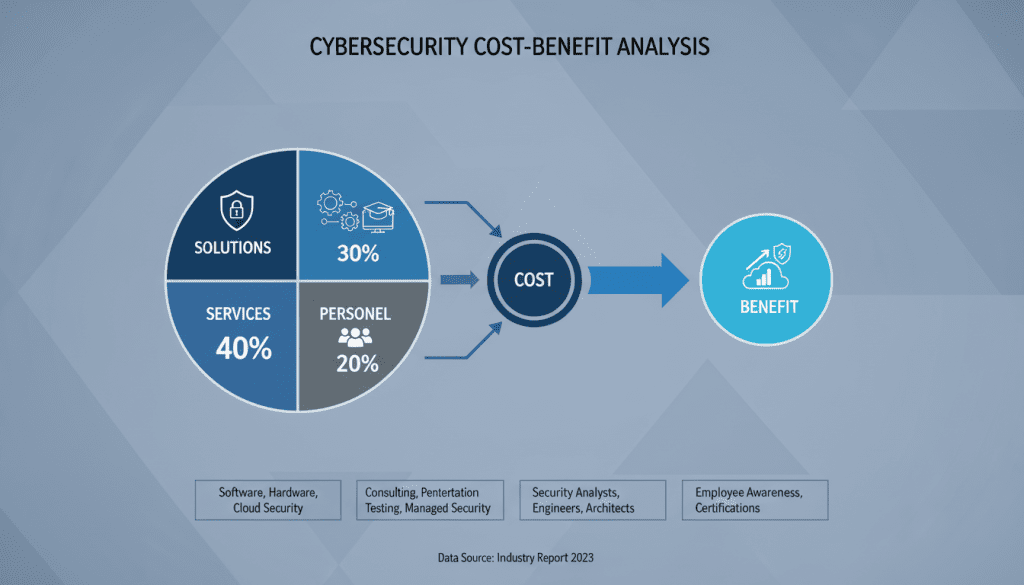
Breakdown of typical cybersecurity investment categories and their relative costs
Cybersecurity spending encompasses multiple components that must be considered in any comprehensive cost-benefit analysis. Understanding these costs is the first step toward evaluating the effectiveness of your security investments.
The technological backbone of your security posture includes firewalls, antivirus software, endpoint protection, intrusion detection systems, and data encryption tools. These solutions typically require both upfront investment and ongoing licensing fees. For enterprise-grade solutions, costs can range from $450 to $2,500 for firewall configurations and $3 to $10 per user monthly for endpoint protection.
Many organizations supplement their internal capabilities with external expertise, including managed security service providers (MSSPs), security assessments, penetration testing, and incident response retainers. These services provide specialized skills without the overhead of full-time staff but can represent significant ongoing expenses ranging from $1,500 to $6,000 for vulnerability assessments.
The human element of cybersecurity includes security analysts, network administrators, compliance officers, and security leadership. According to industry data, security analysts command salaries averaging $90,283 annually, while network administrators typically earn around $63,244 per year. These costs extend beyond base salaries to include benefits, training, and retention expenses.
Effective security requires ongoing education for both technical staff and general employees. Professional certifications like CISSP ($699) and CEH ($1,199) represent significant investments in staff development, while organization-wide security awareness programs can cost $15-40 per employee annually but are essential for reducing human-factor risks.
Beyond the obvious direct expenses, cybersecurity investments incur several indirect costs that must be factored into any comprehensive analysis:

To perform an effective cost-benefit analysis of cybersecurity investments, you must understand what you’re protecting against. The financial consequences of cyber attacks extend far beyond immediate remediation costs and can impact organizations for years after an incident.
Immediate costs include incident response, forensic investigation, data recovery, and system restoration. For ransomware attacks, organizations may face ransom demands averaging $570,000 in 2021. Organizations experiencing cyber attacks report losing between $50,000 and $99,999 in direct revenue on average.
Business downtime represents one of the most significant costs of cyber incidents. With average downtime lasting 21 days following a ransomware attack, organizations face substantial productivity losses, missed opportunities, and inability to serve customers—all translating to revenue impact.
Data breaches often trigger regulatory investigations, potential fines, and litigation. Legal costs alone can range from $50,000 to $148 million, with a median of $1.6 million. Under regulations like GDPR, organizations can face penalties up to €20 million or 4% of global annual revenue.
Perhaps the most difficult impact to quantify is reputational damage. Studies indicate that reputational costs from abnormal customer turnover and loss of goodwill average around $1.57 million per incident. This damage can persist long after systems are restored, affecting customer acquisition, retention, and even valuation for public companies.
“The true cost of a cyber attack extends far beyond the immediate incident response. Organizations must consider the full spectrum of financial impacts when evaluating security investments.”
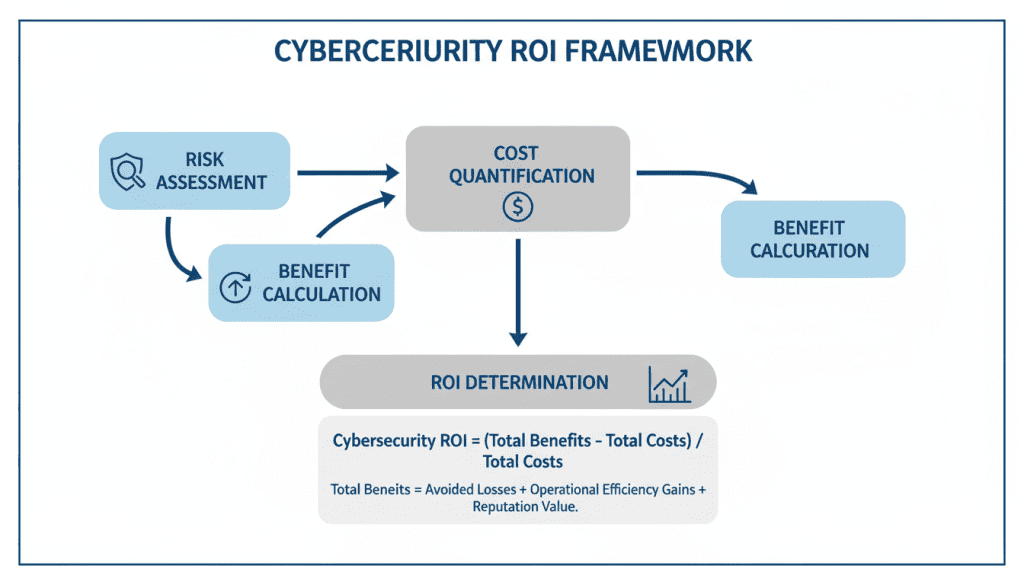
A structured approach to cybersecurity cost-benefit analysis enables organizations to make data-driven decisions about security investments. This framework provides a repeatable methodology for evaluating the financial implications of security controls.
Begin by identifying your organization’s critical assets, potential threats, and existing vulnerabilities. For each scenario, estimate two key variables:
Multiply these values to calculate the Annualized Loss Expectancy (ALE): ALE = SLE × ARO
For each security control under consideration, evaluate its effectiveness in reducing either the probability (ARO) or impact (SLE) of identified threats. This reduction represents the expected benefit of the control in terms of loss avoidance.
Example: If a ransomware attack has an ARO of 0.2 (20% chance annually) and an SLE of $500,000, the ALE is $100,000. If implementing advanced endpoint protection reduces the ARO to 0.05 (5% chance), the new ALE becomes $25,000, representing a $75,000 annual benefit in risk reduction.
Calculate the Total Cost of Ownership (TCO) for each security control, including:
With benefits (reduced ALE) and costs (TCO) quantified, calculate the Return on Investment for each security control:
Cybersecurity ROI = (Expected Loss Reduction – Annualized Cost) / Annualized Cost
Where Expected Loss Reduction = ALE before – ALE after
This formula provides a standardized metric for comparing different security investments and prioritizing those with the highest return relative to cost.
Our Cybersecurity Investment Calculator helps you apply this framework to your specific environment, providing customized insights into your most valuable security investments.

While a structured framework provides clarity, several challenges complicate cybersecurity cost-benefit analysis. Understanding these challenges helps organizations develop more realistic assessments and avoid common pitfalls.
The probabilistic nature of cyber threats introduces significant uncertainty into cost-benefit calculations. Organizations can address this challenge through:
“You can’t manage what you can’t measure—but you also can’t pretend uncertain estimates are precise.”
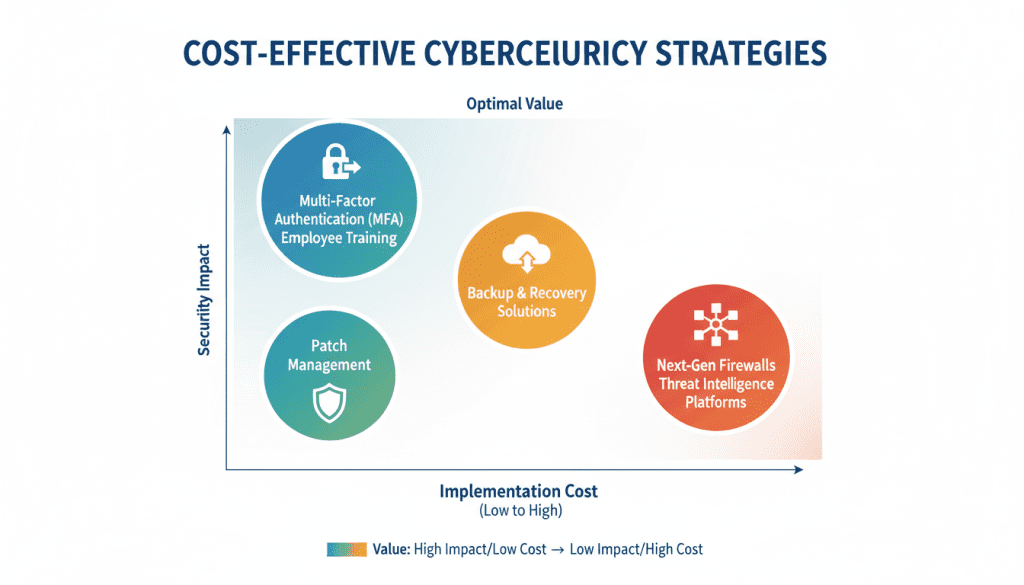
Not all security investments deliver equal value. Organizations with limited resources should prioritize controls that provide the highest security benefit relative to cost. These cost-effective strategies form the foundation of a robust security program while maximizing return on investment.
Implementing MFA can prevent up to 99.9% of account compromise attacks, according to Microsoft research. With relatively low implementation costs ($3-6 per user monthly) and minimal user friction with modern solutions, MFA represents one of the highest-value security investments available.
With human error involved in over 85% of breaches, targeted security awareness programs deliver exceptional ROI. Modern phishing simulation and training platforms cost $15-40 per user annually while significantly reducing successful social engineering attacks.
Timely patching prevents exploitation of known vulnerabilities that attackers frequently target. While requiring process discipline more than financial investment, effective patch management can be implemented with minimal additional tools while dramatically reducing the attack surface.
For many organizations, particularly those with limited internal security expertise, strategic outsourcing can improve security posture while controlling costs:
The Gordon-Loeb economic model provides a mathematical framework for determining optimal cybersecurity investment levels. The model suggests that organizations should generally invest less than 37% of the expected loss from a cybersecurity breach. This guideline helps prevent overinvestment in security controls with diminishing returns.
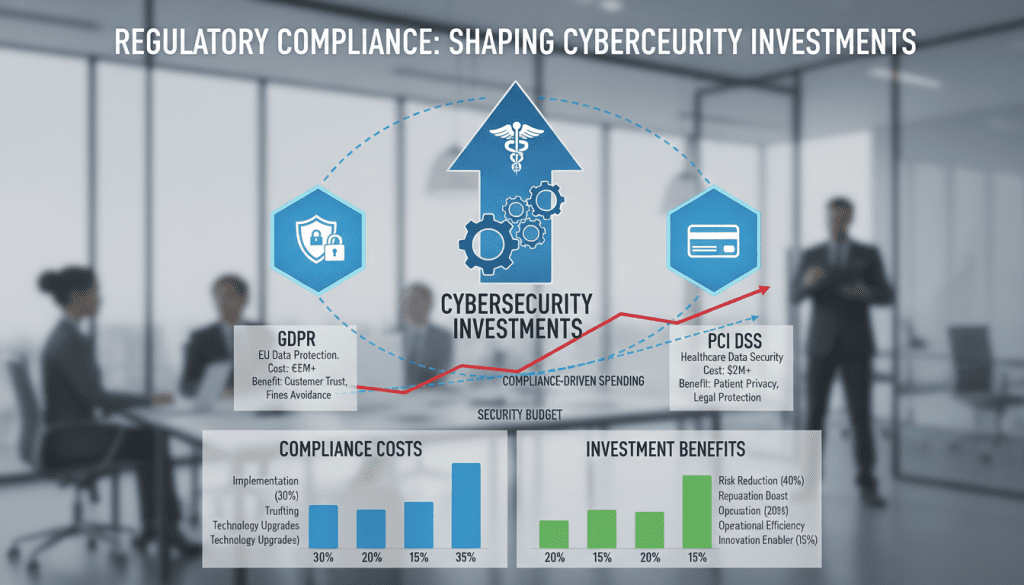
Regulatory requirements significantly influence cybersecurity investments, introducing both mandatory costs and potential strategic benefits. Understanding these impacts is essential for a comprehensive cost-benefit analysis.
Regulatory frameworks like GDPR, HIPAA, PCI DSS, and industry-specific requirements mandate specific security controls and processes. These compliance obligations introduce several cost categories:
| Compliance Cost Category | Description | Typical Investment Range |
| Assessment & Gap Analysis | Initial evaluation of compliance status and required remediation | $10,000 – $50,000 |
| Control Implementation | Technical and procedural controls required by regulations | $50,000 – $500,000+ |
| Documentation & Policies | Development and maintenance of required documentation | $15,000 – $75,000 |
| Audit & Certification | Third-party validation of compliance status | $20,000 – $100,000 annually |
| Ongoing Monitoring | Continuous compliance verification and reporting | $25,000 – $150,000 annually |
While compliance requirements introduce costs, they can also deliver strategic benefits that should be factored into cost-benefit analysis:
Important: Non-compliance can result in significant financial penalties. Under GDPR, organizations can face fines up to €20 million or 4% of global annual revenue, whichever is higher. These potential penalties must be factored into the cost-benefit analysis as risk-based costs.
Translating technical security requirements into business language is essential for securing executive support and budget approval. A compelling business case connects security investments to business outcomes and financial metrics that resonate with decision-makers.
Structure your cybersecurity investment proposal to address key stakeholder concerns:
Address this by quantifying risk reduction through metrics like reduced attack surface, improved detection capabilities, and decreased mean time to respond. Reference industry benchmarks and case studies demonstrating effectiveness of proposed controls.
Calculate and present clear payback periods based on risk reduction. For example: “Implementing MFA at $50,000 annually reduces our ALE by $250,000, providing a 5x return and payback period of approximately 10 weeks.”
Present a monitoring framework with specific KPIs such as security incidents prevented, mean time to detect/respond, patch compliance rates, and user awareness metrics. Commit to regular reporting on these metrics to demonstrate ongoing value.
Emphasize that cybersecurity cost-benefit analysis is not a one-time exercise but an ongoing process:
Effective cybersecurity cost-benefit analysis transforms security from a technical necessity into a strategic business enabler. By quantifying both the costs of security controls and the financial benefits of risk reduction, organizations can make informed decisions that optimize resource allocation while protecting critical assets.
The most successful security programs balance investment with risk appetite, focusing first on high-impact, low-cost controls that deliver exceptional ROI. By applying the frameworks and methodologies outlined in this guide, security leaders can build compelling business cases that secure executive support and demonstrate ongoing value.
Remember that cybersecurity is not about eliminating all risk—an impossible goal—but rather about making strategic investments that reduce risk to acceptable levels while enabling business objectives. A disciplined, data-driven approach to cybersecurity cost-benefit analysis provides the foundation for this balanced security strategy.
Download our Cybersecurity ROI Calculator and Investment Framework to apply these principles to your organization. Our tool helps you quantify security risks, evaluate control effectiveness, and build compelling business cases for your most critical security investments.
Experience power, efficiency, and rapid scaling with Cloud Platforms!