Selecting the right cloud security provider has become a critical decision for organizations as cloud environments grow increasingly complex. With evolving threats, compliance requirements, and multi-cloud deployments, the stakes of this choice have never been higher. This comprehensive guide will walk you through the essential evaluation criteria, comparison frameworks, and practical steps to select a cloud security provider that aligns with your organization’s unique security needs. Why Cloud Security Provider Selection Matters More Than Ever
The rapid adoption of cloud services has fundamentally changed how organizations approach security. Traditional perimeter-based defenses are no longer sufficient as data and workloads move beyond corporate networks. According to recent studies, over 78% of organizations now use two or more cloud providers, creating expanded attack surfaces and security blind spots.
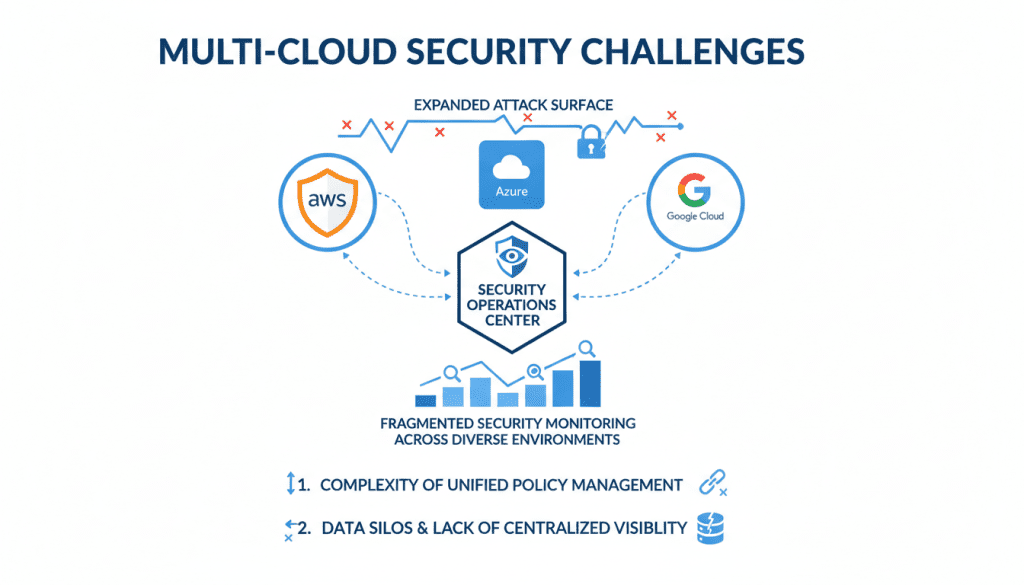
Fig 1: The expanding attack surface in multi-cloud environments requires strategic cloud security provider selection
Choosing the wrong cloud security provider can result in devastating consequences. The average cost of a cloud data breach now exceeds $4.5 million, while regulatory penalties under frameworks like GDPR can reach up to 4% of global annual revenue. Beyond financial impact, security failures damage customer trust and brand reputation in ways that can take years to rebuild.
Not Sure Where to Start?
Our cloud security experts can help you navigate the complex provider landscape and identify the right security partner for your specific needs.
Schedule a Selection Consultation
Understanding Your Cloud Security Requirements
Before evaluating providers, you must clearly define your organization’s unique security requirements. This foundation ensures you select a provider that addresses your specific challenges rather than being swayed by marketing claims or feature lists.
Assessing Your Cloud Environment Complexity
The complexity of your cloud environment directly impacts your security requirements. Organizations with hybrid or multi-cloud deployments face different challenges than those using a single cloud provider. Consider these factors when defining your needs:
Cloud Deployment Models
- Single public cloud (AWS, Azure, GCP)
- Multi-cloud deployment
- Hybrid cloud (public + private)
- Cloud-native applications
Workload Types
- Virtual machines
- Containers and Kubernetes
- Serverless functions
- PaaS and SaaS applications
Regulatory and Compliance Requirements
Your industry and geographic location determine which compliance frameworks apply to your organization. Cloud security providers must support these requirements through appropriate controls, documentation, and certifications.
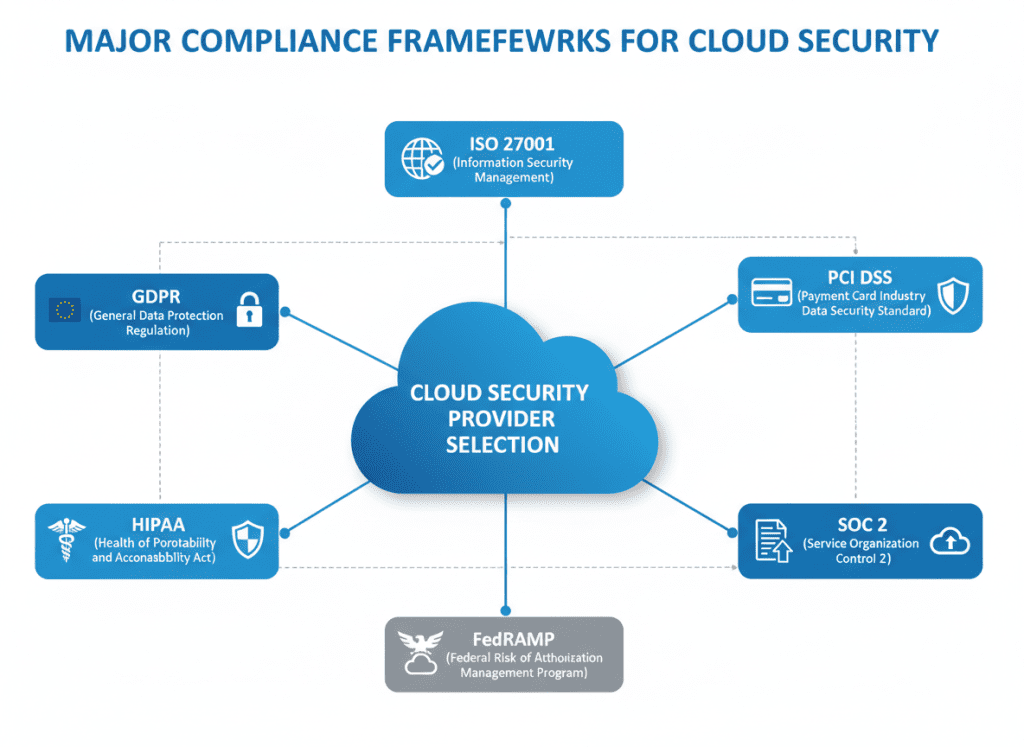
Fig 2: Key compliance frameworks to consider during cloud security provider selection
| Compliance Framework | Industry Focus | Key Security Requirements |
| GDPR | All industries (EU data) | Data protection, privacy controls, breach notification |
| HIPAA | Healthcare | PHI protection, access controls, audit logging |
| PCI DSS | Payment processing | Cardholder data protection, network security |
| SOC 2 | Service organizations | Security, availability, processing integrity |
| ISO 27001 | All industries | Information security management system |
| FedRAMP | Government | Standardized security assessment for cloud services |
Risk Profile and Threat Landscape
Different organizations face different threat landscapes based on their industry, data sensitivity, and business operations. Your cloud security provider selection should align with your specific risk profile and the threats most likely to target your organization.
Define Your Security Requirements
Our experts can help you identify your unique cloud security requirements based on your environment, compliance needs, and risk profile.
Get Custom Requirements Assessment
Essential Features for Cloud Security Provider Selection
When evaluating cloud security providers, certain core capabilities are non-negotiable. These foundational features form the baseline for effective cloud security and should be present in any provider you consider.
Identity and Access Management
Identity has become the new security perimeter in cloud environments. Effective identity and access management (IAM) is critical for controlling who can access your cloud resources and what actions they can perform.
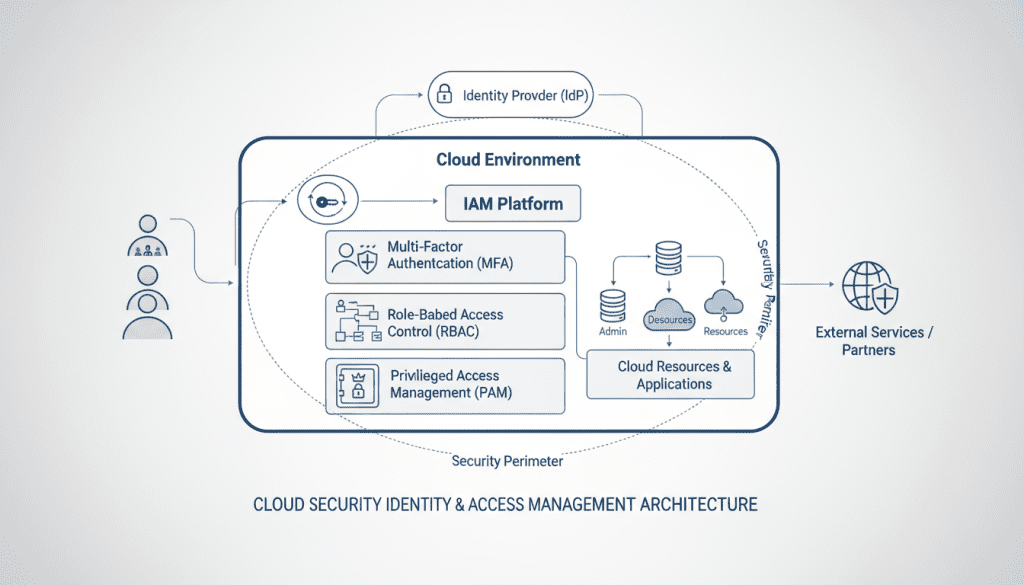
Fig 3: Comprehensive IAM architecture for secure cloud environments
Look for providers that offer:
- Role-based access control (RBAC) with least privilege enforcement
- Multi-factor authentication (MFA) for all administrative access
- Just-in-time (JIT) privileged access management
- Integration with enterprise identity providers (Azure AD, Okta)
- Automated access reviews and certification
- Anomalous behavior detection for identity threats
Data Protection and Encryption
Comprehensive data protection is essential for safeguarding sensitive information in the cloud. Your provider should offer robust encryption capabilities for data at rest, in transit, and ideally, in use.
Key capabilities to evaluate include:
- AES-256 encryption for data at rest
- TLS 1.3 for data in transit
- Customer-managed encryption keys (CMEK)
- Hardware Security Module (HSM) support
- Key rotation and lifecycle management
- Data loss prevention (DLP) capabilities
- Secure key storage and backup
Threat Detection and Response
Cloud environments face a constantly evolving threat landscape. Your security provider must offer advanced detection and response capabilities to identify and mitigate threats quickly.
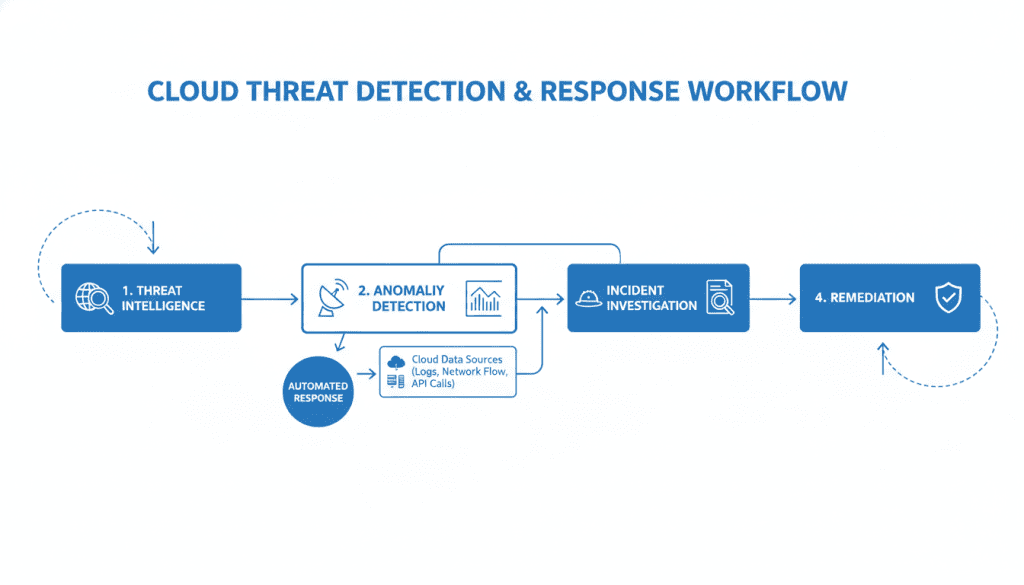
Fig 4: Effective cloud threat detection and response workflow
Essential threat detection and response features include:
- Real-time monitoring across cloud services and workloads
- Advanced analytics and machine learning for anomaly detection
- Integration with threat intelligence feeds
- Automated response capabilities for common threats
- Incident investigation and forensics tools
- Cross-cloud visibility and correlation
Evaluate Your Current Security Gaps
Our cloud security assessment can identify gaps in your current protection and help you prioritize features when selecting a provider.
Request Security Gap Analysis
Advanced Capabilities to Consider in Cloud Security Provider Selection
Beyond core features, leading cloud security providers offer advanced capabilities that can provide significant additional protection. These features may be particularly important depending on your specific environment and risk profile.
Cloud Security Posture Management (CSPM)
CSPM tools continuously monitor your cloud environment for misconfigurations, compliance violations, and security risks. This proactive approach helps prevent breaches before they occur.
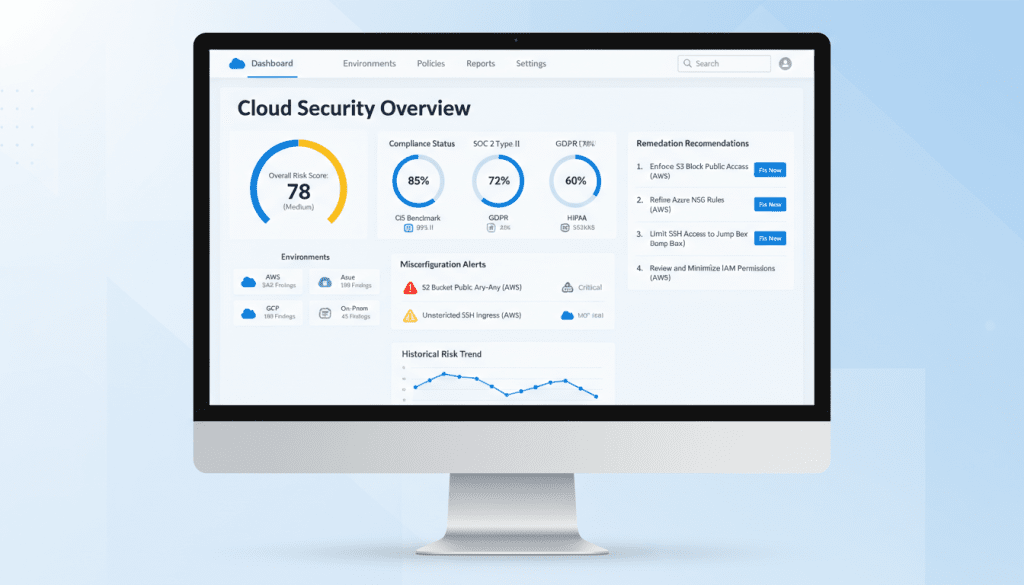
Fig 5: CSPM dashboard showing cloud configuration risks and compliance status
Key CSPM capabilities to evaluate:
- Continuous scanning for misconfigurations and policy violations
- Multi-cloud support (AWS, Azure, GCP)
- Compliance benchmarking against industry standards
- Automated remediation workflows
- Risk prioritization based on potential impact
- Integration with DevOps workflows
Cloud Workload Protection Platform (CWPP)
CWPP solutions protect the workloads running in your cloud environment, including virtual machines, containers, and serverless functions. These tools provide runtime protection against threats targeting your applications and data.
Important CWPP features include:
- Runtime application self-protection (RASP)
- Container security and Kubernetes protection
- Memory protection against zero-day exploits
- File integrity monitoring
- Behavioral monitoring and anomaly detection
- Vulnerability management and virtual patching
Cloud Infrastructure Entitlement Management (CIEM)
CIEM solutions address the challenge of managing identities and permissions across complex cloud environments. These tools help enforce least privilege and reduce the risk of permission sprawl.
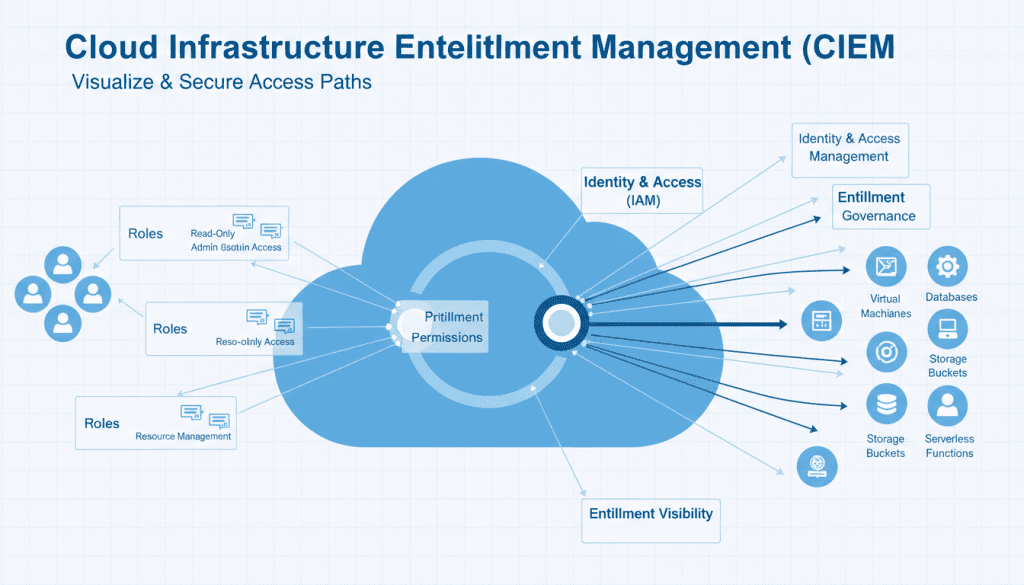
Fig 6: CIEM visualization showing identity and permission relationships
Key CIEM capabilities to consider:
- Discovery of all identities and permissions across clouds
- Identification of excessive, unused, or risky permissions
- Right-sizing of permissions based on actual usage
- Automated remediation of permission issues
- Continuous monitoring for permission changes
- Integration with identity governance systems
Operational Considerations for Cloud Security Provider Selection
Beyond technical capabilities, operational factors play a crucial role in the success of your cloud security strategy. These considerations affect how well the provider’s solutions integrate with your existing processes and support your security team.
Integration with Existing Security Stack
Your cloud security provider should integrate seamlessly with your existing security tools and processes to provide unified protection and visibility.
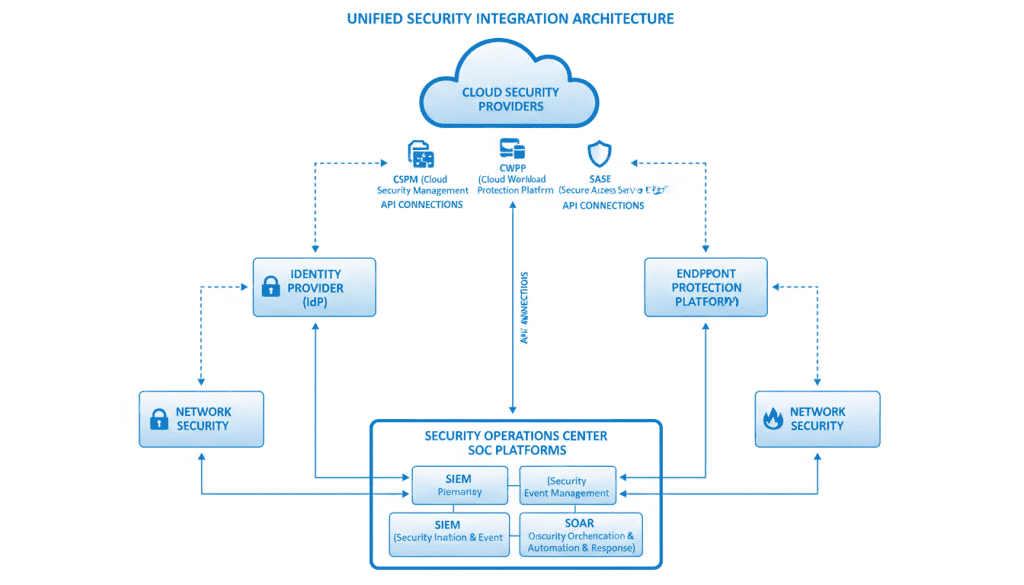
Fig 7: Integration architecture between cloud security and existing security tools
Key integration points to evaluate:
- SIEM integration for centralized logging and alerting
- SOAR integration for automated response workflows
- API availability and documentation quality
- Integration with identity providers and directory services
- Support for security orchestration across tools
- Custom integration capabilities and professional services
Scalability and Performance
As your cloud environment grows, your security solutions must scale accordingly without compromising performance or creating bottlenecks.
Scalability factors to consider:
- Support for large-scale deployments (thousands of resources)
- Performance impact on protected workloads
- Ability to handle burst traffic and rapid scaling
- Distributed architecture for high availability
- Resource requirements and optimization
- Cost scaling models as environment grows
Managed Services and Support
Given the complexity of cloud security and the shortage of skilled security professionals, managed services and expert support can be valuable components of your security strategy.

Fig 8: Managed security operations for cloud environments
Support and managed service considerations:
- 24/7 monitoring and response capabilities
- Expertise in your specific cloud platforms
- Incident response support and SLAs
- Proactive threat hunting services
- Implementation and configuration assistance
- Training and knowledge transfer for your team
Need Help Evaluating Providers?
Our cloud security experts can help you assess providers against your specific operational requirements and integration needs.
Schedule Provider Evaluation Session
Cloud Security Provider Selection Framework
A structured evaluation framework helps ensure you consider all relevant factors when selecting a cloud security provider. This approach allows for objective comparison and defensible decision-making.
Defining Evaluation Criteria
Start by defining the specific criteria that matter most to your organization. These should align with your security requirements, risk profile, and operational needs.
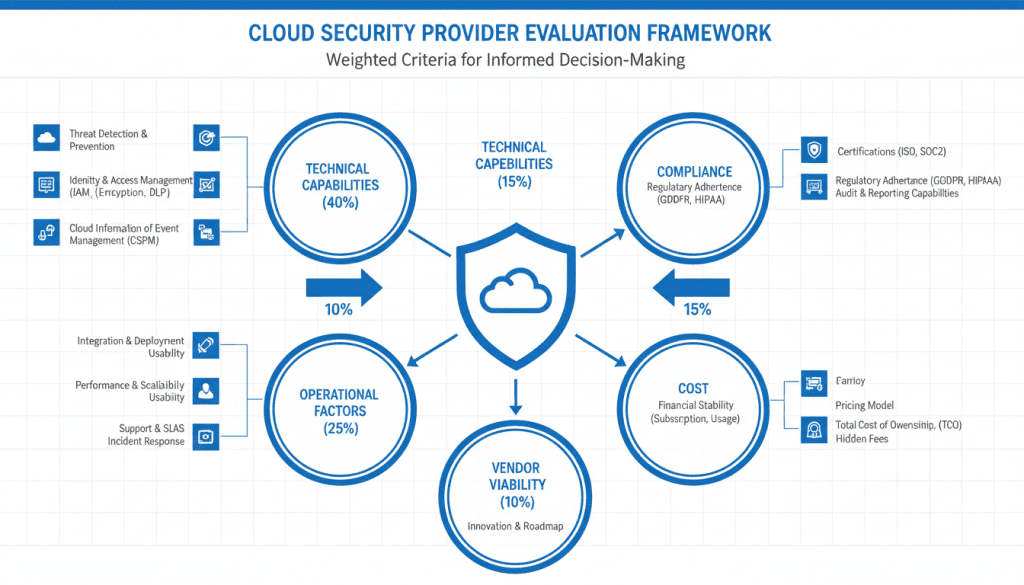
Fig 9: Structured evaluation framework with weighted criteria categories
Sample evaluation categories and weights:
| Category | Weight | Sample Criteria |
| Technical Capabilities | 40% | IAM, encryption, threat detection, CSPM, CWPP, CIEM |
| Operational Factors | 25% | Integration, scalability, usability, support, managed services |
| Compliance & Governance | 15% | Certifications, audit support, policy management |
| Cost & Value | 10% | Licensing model, TCO, ROI, cost predictability |
| Vendor Viability | 10% | Market position, financial stability, roadmap, innovation |
Scoring Methodology
Develop a consistent scoring approach to evaluate providers against your criteria. This enables objective comparison and helps justify your selection decision.
Sample scoring methodology:
- Score each criterion on a scale of 1-5 (1 = poor, 5 = excellent)
- Multiply criterion scores by category weights
- Sum weighted scores for overall provider rating
- Document strengths and weaknesses for each provider
- Identify any “must-have” requirements that are non-negotiable
Proof of Concept (PoC) Testing
For shortlisted providers, conduct hands-on testing in your environment to validate capabilities and performance. This real-world evaluation provides insights that documentation and demos cannot.
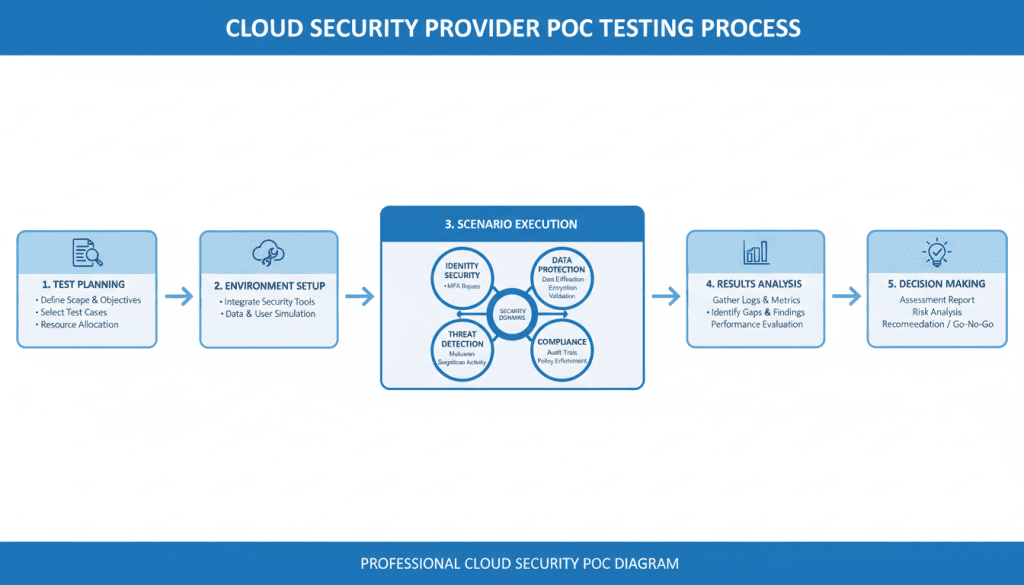
Fig 10: Structured PoC testing process for cloud security providers
Key PoC scenarios to test:
- Identity compromise detection and response
- Data protection effectiveness (encryption, access controls)
- Misconfiguration identification and remediation
- Threat detection and response capabilities
- Integration with existing security tools
- Performance impact on cloud workloads
- Usability and workflow efficiency
Streamline Your Evaluation Process
Download our comprehensive Cloud Security Provider Comparison Checklist to accelerate your evaluation process and ensure you consider all critical factors.
Download Comparison Checklist
Leading Cloud Security Providers in 2026
While your specific requirements should drive your selection process, understanding the strengths and focus areas of leading providers can help inform your evaluation. Here’s an overview of notable cloud security providers in 2026.
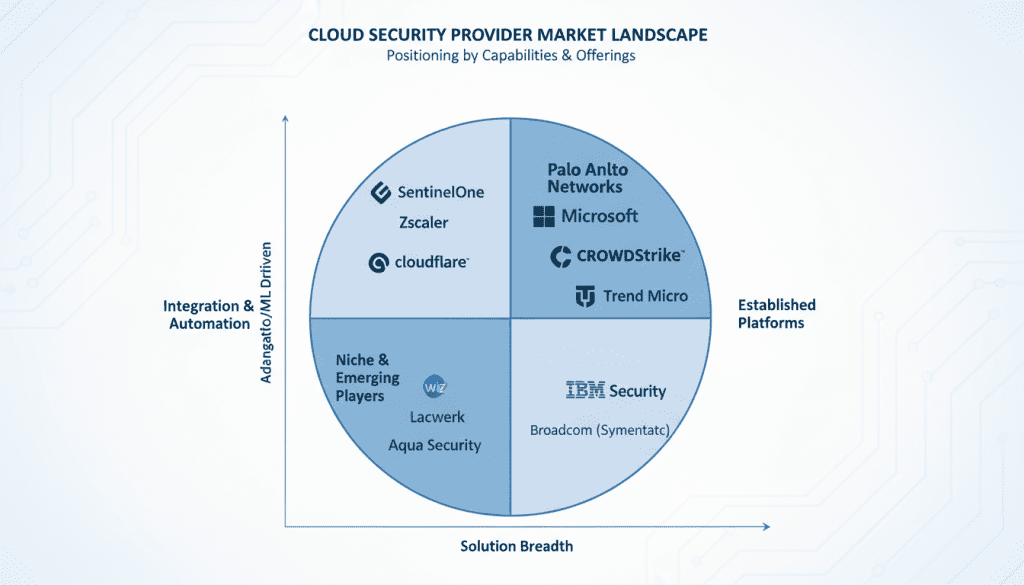
Fig 11: Cloud security provider market landscape 2026
Cloud-Native Security Specialists
These providers focus exclusively on cloud security with purpose-built solutions for cloud environments.
- Strong CSPM and CWPP capabilities
- Deep integration with cloud provider APIs
- DevSecOps-friendly workflows
- Rapid innovation and feature development
Enterprise Security Leaders
Established security vendors with comprehensive portfolios spanning cloud and on-premises environments.
- Integrated security platforms
- Strong threat intelligence capabilities
- Mature support and services
- Broad compliance certifications
Cloud Provider Security
Native security offerings from major cloud service providers (AWS, Azure, GCP).
- Deep integration with cloud platforms
- Simplified deployment and management
- Consistent updates with platform features
- Consolidated billing and support
Key Differentiators to Consider
When evaluating providers, pay attention to these differentiating factors that may impact their suitability for your needs:
- Multi-cloud vs. single-cloud focus and capabilities
- Agent-based vs. agentless deployment models
- Platform approach vs. point solutions
- Managed service options and professional services
- Specialized capabilities for your industry or compliance needs
- Innovation pace and product roadmap alignment
- Pricing models and total cost of ownership
Implementation Best Practices After Cloud Security Provider Selection
Selecting the right provider is just the beginning. Successful implementation requires careful planning, phased deployment, and ongoing optimization to maximize the value of your cloud security investment.
Deployment Planning
Develop a structured implementation plan that addresses technical, operational, and organizational considerations.
- Conduct a detailed discovery of your cloud environment
- Define success criteria and key performance indicators
- Create a phased deployment roadmap with milestones
- Identify integration points with existing systems
- Develop testing and validation procedures
- Plan for knowledge transfer and team training
Phased Implementation Approach
A phased approach reduces risk and allows for adjustment based on initial results. Consider this sample implementation sequence:
| Phase | Focus Areas | Duration |
| 1: Foundation | Environment discovery, baseline policies, initial monitoring | 2-4 weeks |
| 2: Core Protection | IAM controls, encryption, CSPM implementation | 4-6 weeks |
| 3: Advanced Security | Threat detection, CWPP, CIEM deployment | 6-8 weeks |
| 4: Integration | SIEM/SOAR integration, workflow automation | 4-6 weeks |
| 5: Optimization | Fine-tuning, advanced use cases, ongoing improvement | Continuous |
Measuring Success and Continuous Improvement
Establish metrics to evaluate the effectiveness of your cloud security implementation and identify areas for improvement.
Key performance indicators to track:
- Time to detect and respond to security incidents
- Reduction in cloud misconfigurations and policy violations
- Coverage of cloud resources under security controls
- Security team efficiency and alert quality
- Compliance posture and audit readiness
- Total cost of ownership and ROI
Need Implementation Support?
Our cloud security experts can help you develop a tailored implementation plan and provide guidance throughout your deployment journey.
Request Implementation Consultation
Conclusion: Making the Right Cloud Security Provider Selection
Selecting the right cloud security provider is a critical decision that impacts your organization’s risk posture, operational efficiency, and ability to innovate securely in the cloud. By following a structured evaluation process that aligns with your specific requirements, you can make a confident, defensible selection that delivers long-term value.
Remember these key principles throughout your selection journey:
- Start with a clear understanding of your unique security requirements
- Evaluate providers against objective, weighted criteria
- Validate capabilities through hands-on testing in your environment
- Consider both technical and operational factors in your decision
- Plan for successful implementation with a phased approach
- Measure outcomes and continuously optimize your security posture
With the right cloud security provider as your partner, you can confidently accelerate your cloud journey while maintaining strong protection for your critical assets and data.
Ready to Find Your Ideal Cloud Security Partner?
Our experts can guide you through the entire selection process, from requirements definition to final decision and implementation planning.
Start Your Selection Journey Today
Frequently Asked Questions About Cloud Security Provider Selection
How long should the cloud security provider selection process take?
The timeline varies based on organization size and complexity, but typically ranges from 6-12 weeks for a thorough process. This includes requirements definition (1-2 weeks), initial research and RFI (2-3 weeks), detailed evaluation and PoC testing (3-4 weeks), and final selection and contracting (2-3 weeks).
Should we prioritize a unified platform or best-of-breed point solutions?
This depends on your specific needs. Unified platforms offer simplified management, consistent policies, and integrated workflows, but may not excel in every capability area. Best-of-breed solutions provide superior capabilities in specific areas but require more integration effort and may create visibility gaps. Many organizations adopt a hybrid approach with a core platform supplemented by specialized tools for critical capabilities.
How important are analyst ratings like Gartner and Forrester in the selection process?
Analyst ratings provide valuable market perspective and can help identify leading providers, but should not be the sole basis for selection. These ratings often emphasize breadth of capabilities and market presence over specific fit for your requirements. Use them as an input to your process, but prioritize your unique needs, hands-on testing, and reference checks from organizations similar to yours.
What role should cloud service providers’ native security tools play in our strategy?
Native security tools from cloud providers (AWS, Azure, GCP) offer tight integration, simplified deployment, and often lower cost. They work well for organizations using primarily one cloud platform with moderate security requirements. However, they may lack advanced capabilities, multi-cloud support, and independent security validation. Many organizations use native tools for foundational security and third-party solutions for advanced protection and multi-cloud consistency.
How should we evaluate the total cost of ownership for cloud security solutions?
Look beyond license costs to include implementation, integration, ongoing management, and potential cost savings. Consider factors like resource requirements (staff time, expertise), training needs, efficiency improvements, and risk reduction value. Also evaluate pricing models (per-user, per-resource, consumption-based) against your growth projections to understand how costs will scale with your environment.





















